Hello I’m Abzee.
I will be the one walking you through the CTF i participated which is very fun and I learnt a lot.
ShellCTF 2022 which is organise by Shellpwn Team the CTF lasted from 15:30 EAT of August 12th to 15:30 EAT of 14th of August so i decided to share the walkthrough of the challenges I did by myself.
Misc: World’s Greatest Detective
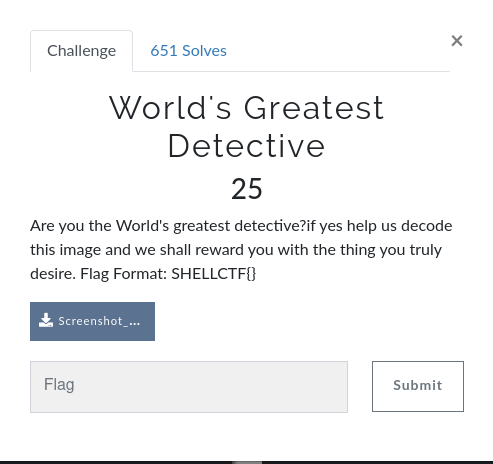
So we downloaded the png file but it was a strange one thou but looking at the png file name it’s said Wakanda_Translator. I quickly rush to my browser and search for Wakanda Translator cipher online.
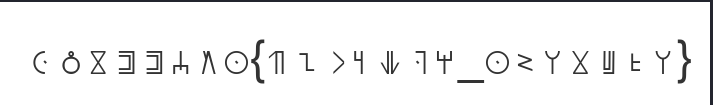
Using this site https://www.dcode.fr/wakanda-alphabet I was able to decrypt the msg and got our flag.
Flag: SHELLCTF{W4kandA_F0rev3r}.
Easy Peasy right.
Crypto: Tweeeet
These was really easy pals after we downloaded the jpeg file we were task to find out what are the birds sitting on the wire are trying to say.

First of all I rush to google and search about birds cipher online to check maybe I can get anything but guess what we where able to find one by using this this link https://www.dcode.fr/birds-on-a-wire-cipher.
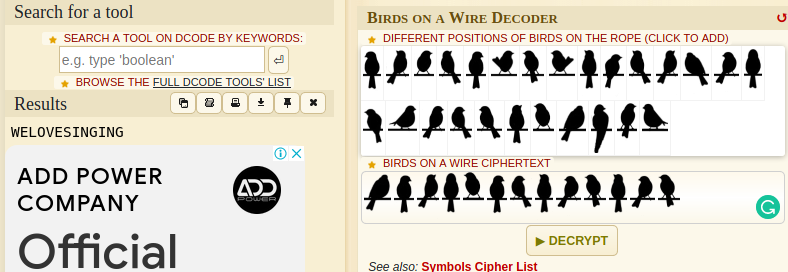
Boom we have our flag: SHELL{WELOVESINGING}.
Crypto: Tring Tring….
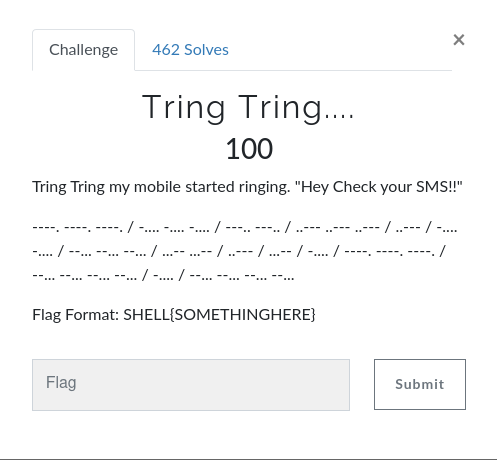
We all know that this is a Morse code cipher but that’s not the end of the encryption. Let check it out and see what we are going to get, So I decided to use online tools called Cyberchef.com.
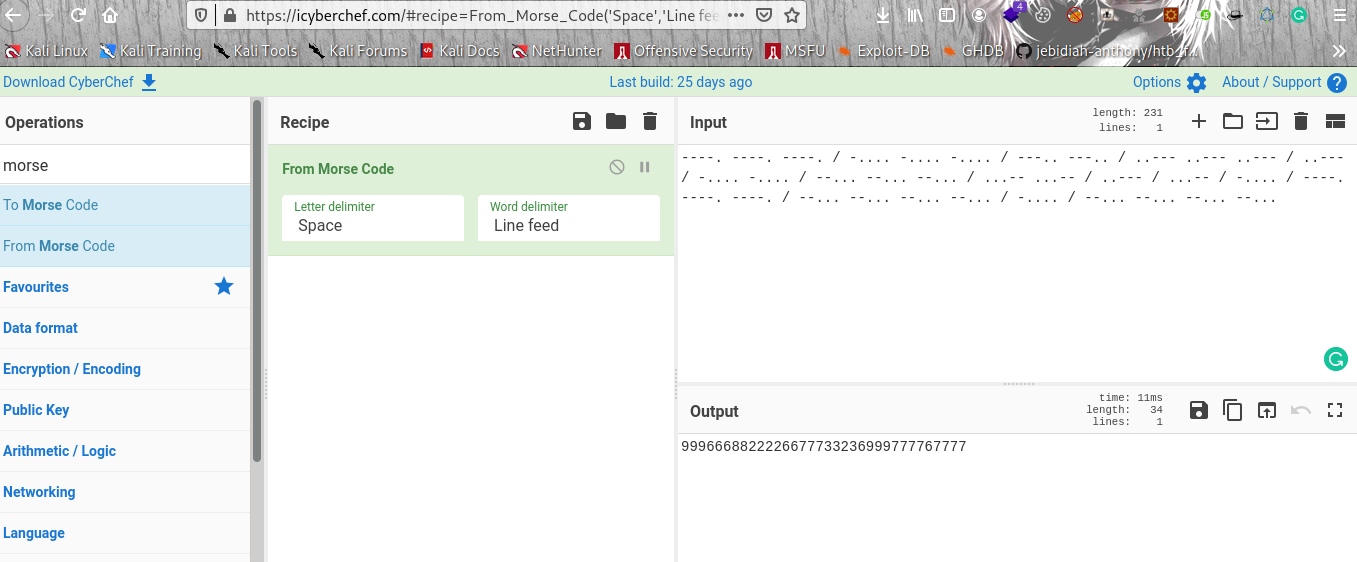
Hmmm interesting I think we got a number when decrypting the Morse code and that number look like an SMS phone code. So quickly search for SMS phone code cipher online and I got one using this link https://www.dcode.fr/multitap-abc-cipher.
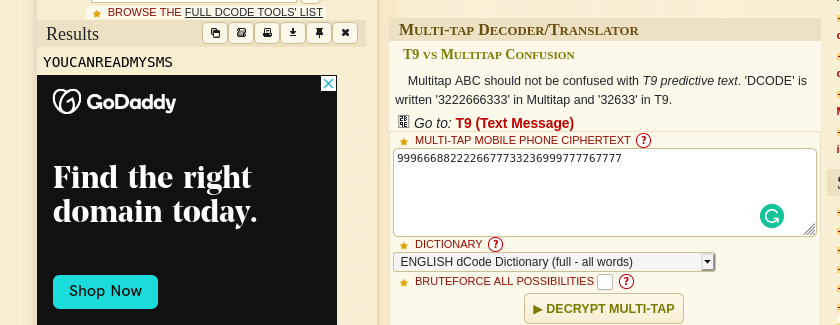
Subarashii we where able to get the flag: SHELL{YOUCANREADMYSMS}.
Crypto: MALBORNE
This challs really gave me a tough time after doing a lot of research I decided to use the header of the challenge which is Malborne. From trying and error i was able to get a site that look similar to the name of the challs so I decided to give a shot and guess what buddy the flag just pop up using this site https://malbolge.doleczek.pl/.
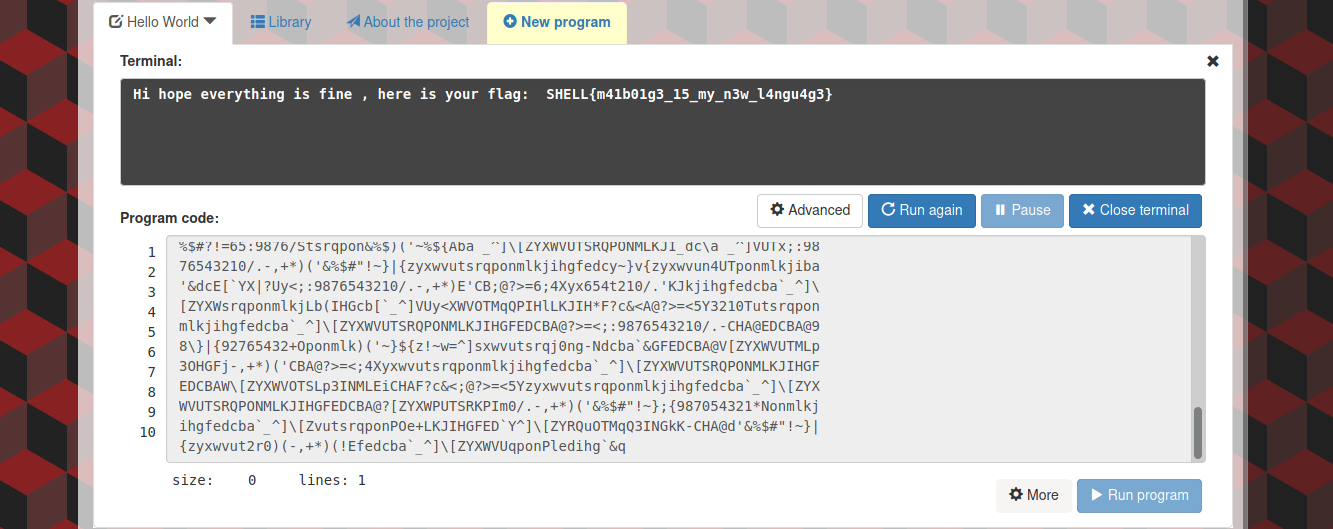
Now we have the flag: SHELL{m41b01g3_15_my_n3w_l4ngu4g3}
Crypto: OX9OR2
Finally we are dealing with python crypto thou I’m not too good in python but this one is quite easy that I decided to use two ways to get the flag.

First of all I check the content of the encryption.py and the encrypted file. So before we can run anything here we have to know the key of the encrypted file so I decided to write a code out and name it exp.py.

This is the python code that I wrote so that I will be able to get the key.
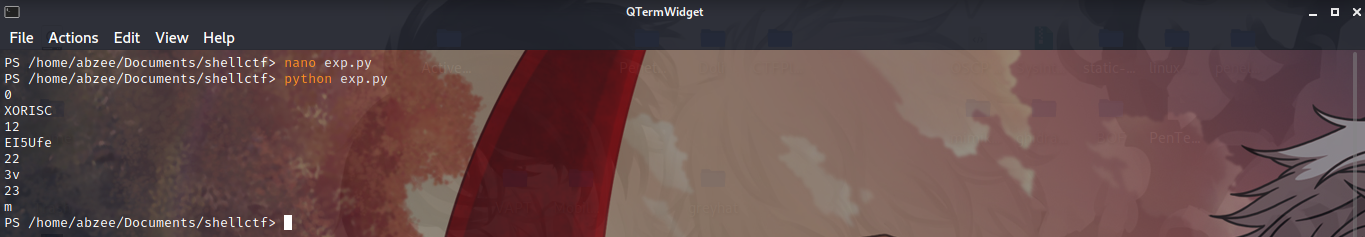
After executing it there is something that caught my eye there which is XORISC in the image above. That’s means we have gotten half of our key which you can brute force for the rest and also guess it so the missing part I guess it by myself as XORISCOOL because it really make sense like that don’t you think so Lol.
Now that we have gotten the Key which is XORISCOOL. I wrote a new code so that the key can be fit in I named It exploit.py.
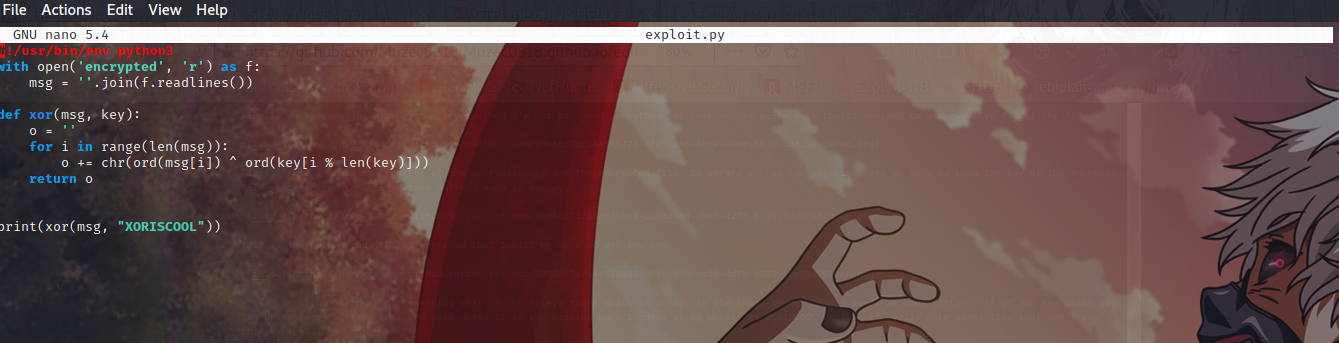
Now let run it with python3 and confirm maybe we are right.
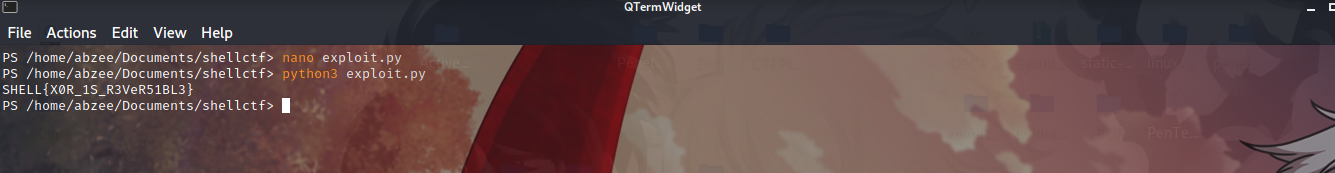
Wow look like it work, Here goes our flag: SHELL{X0R_1S_R3VeR51BL3}.
The other way to get the flag is using Cyberchef unless you know the key.
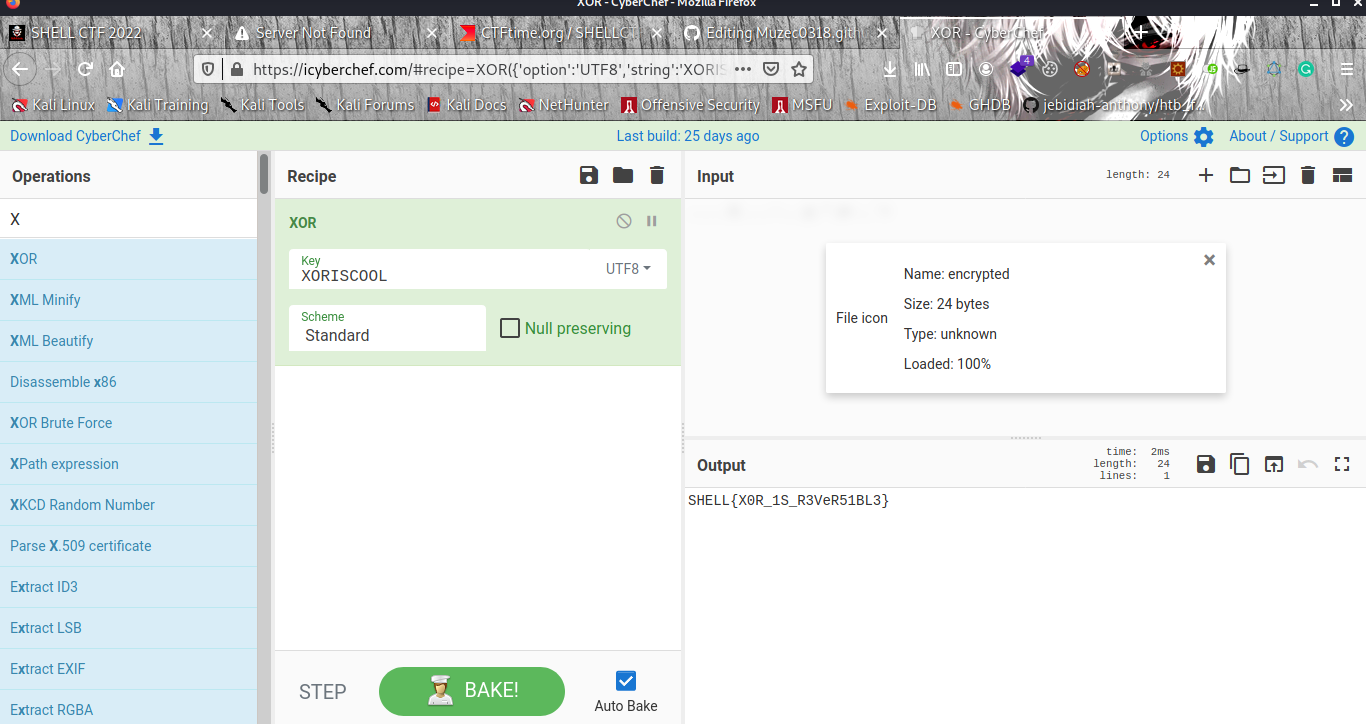
By uploading the encrypted file and knowing the key we where able to get the flag.
Forensics: Alien Communication
Let downloaded the audio and use Sonic visualization on it maybe we can get something from it.
Next step to take is to add it to your Spectrogram and check.
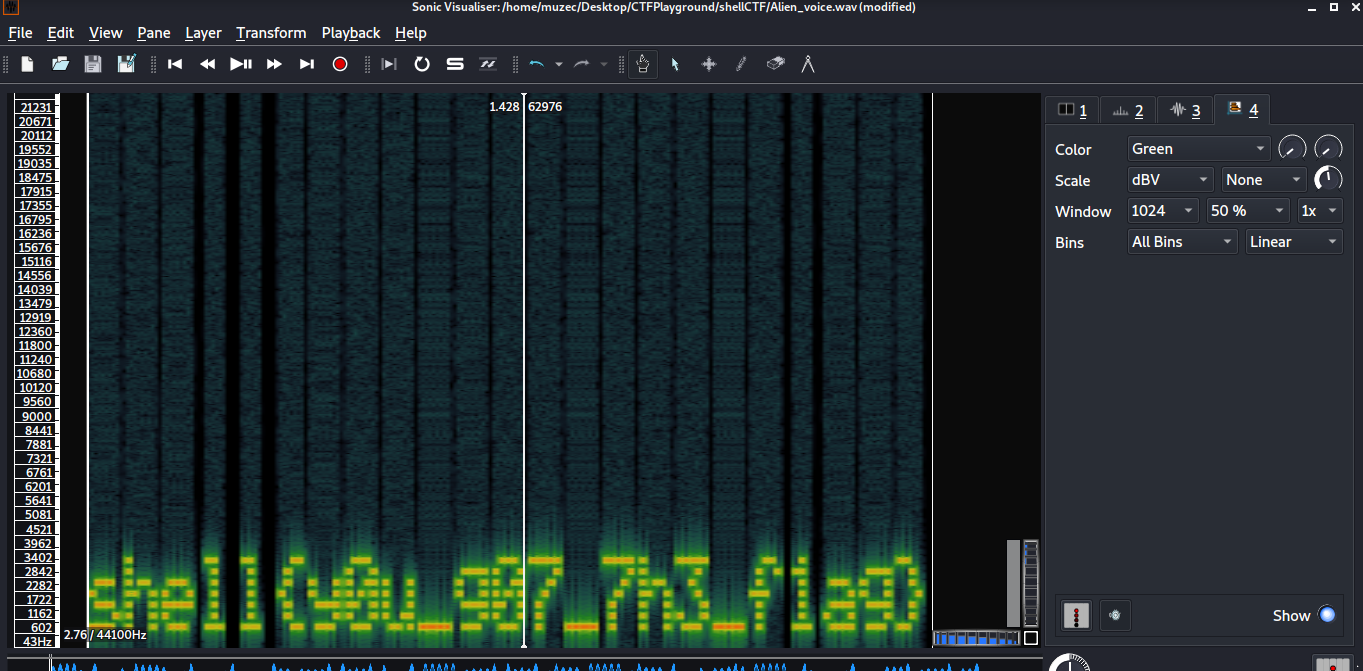
There goes our flag: SHELL{y0u_g07_7h3_f1ag}.
Forensics: Secret Document
Looking at the description of the challenge we are already been given the key which is shell and a hint which is Xorry. Should know in your mind that xorry means from xor so I quickly rush to cyberchef after I downloaded the data.
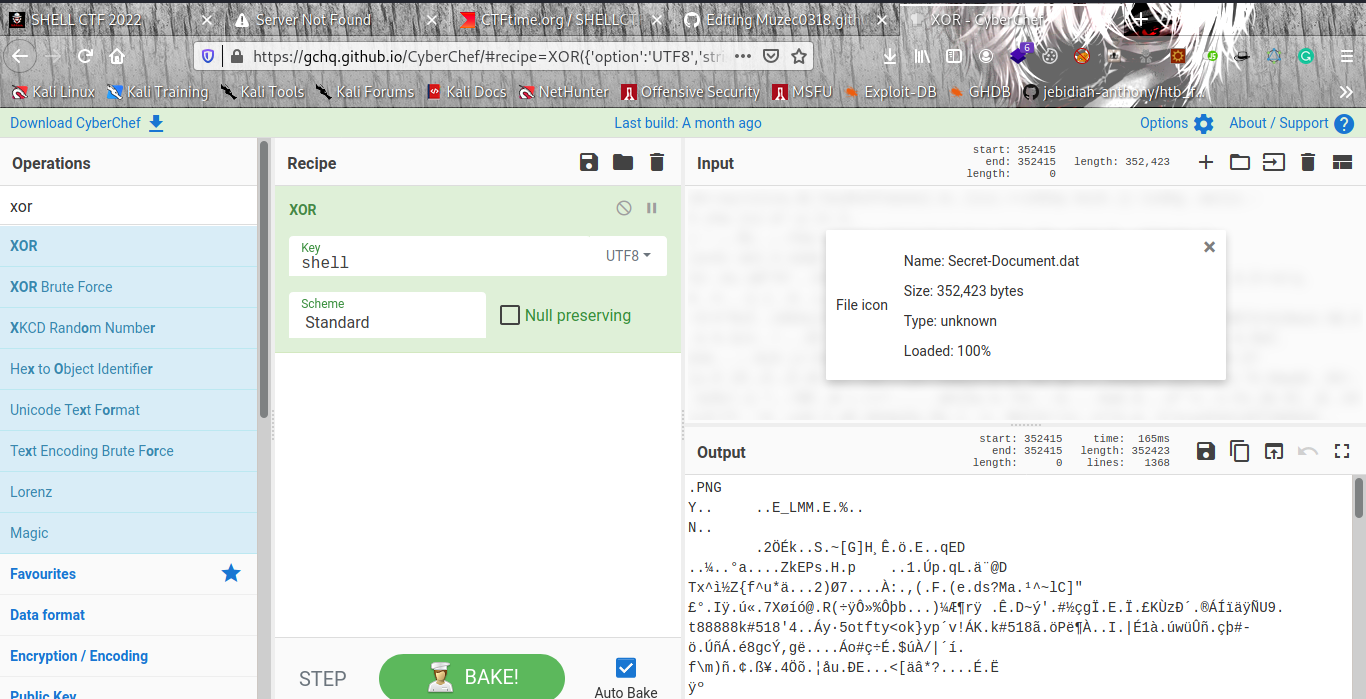
I uploaded it to cyberchef then choose from Xor and put the key that was given and If you can see the data is showining us that it PNG image. Now all we have to do is to convert it to image,
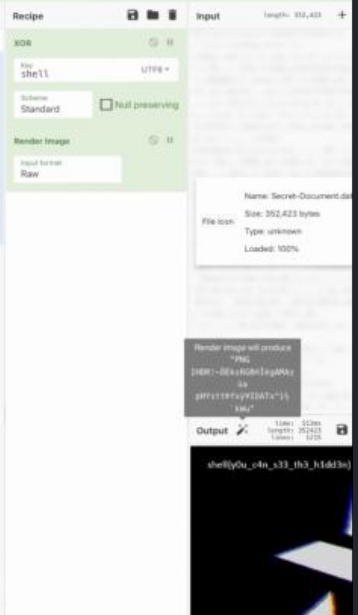
Here goes our flag: SHELL{y0u_c4n_s33_th3_h1dd3n}.
Forensics: Hidden File
First of all let download the jpg image and try a tools call Exiftool on it.
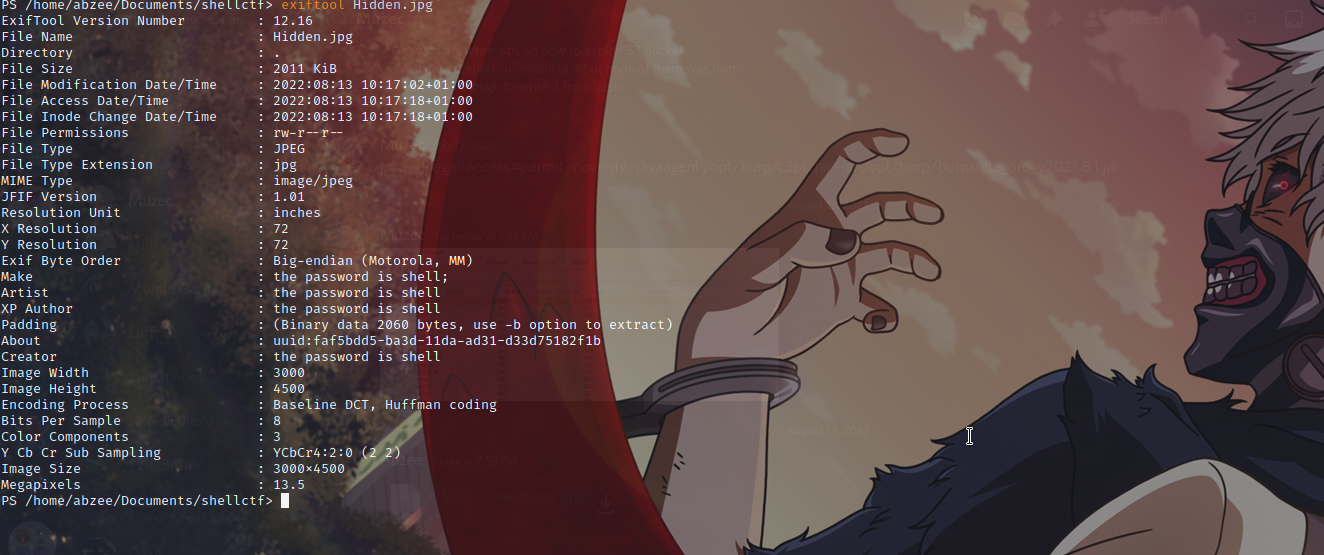
If can see there is a password there which is shell so let try steghide on the image.
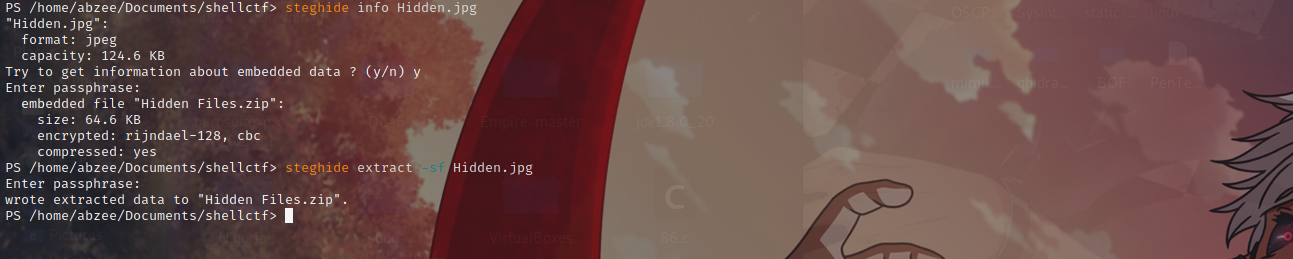
Using steghide we were able to get a hidden zip file. Now let unzip the file with a command called unzip.

When unzipping it we were able to retrieve three file which is se3cretf1l3.pdf, something.jpg and flag.zip. When trying to unzip the flag.zip it was asking for password then i started digging to see maybe i can see something, first of all i tried zip2john but i got not then i decided to go through se3cretf1l3.pdf and look well then i got the password for flag.zip file.

As you can see the password is shellctf. Now let unzip it with the password.
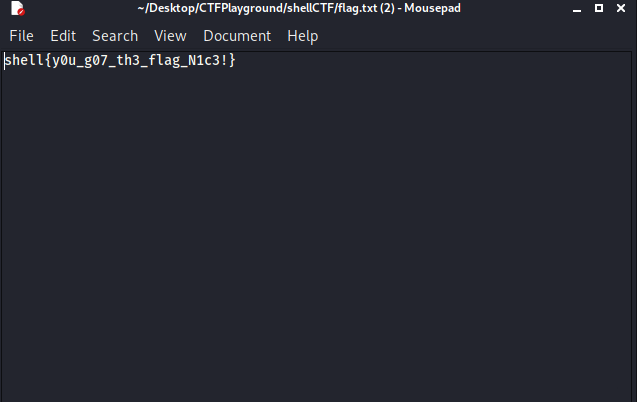
After unzipping it we were able to get our flag: shell{y0u_g07_th3_flag_N1c3!}.