Description
In this lab you will have to use and configure Nessus in order to perform a vulnerability scan against the target machine. However you are not told where the target machine is in the network. You only know it is in the same lab network you are connected to.
Goal
The goal of this lab is to learn how to properly configure Nessus depending on the services running on the target machine.
Tools To Be Use
Fping
Nmap
Nessus
Metasploit
Now The First Step Is To Find A Target In The Network
Since we do not have any information about our lab network and the hosts attached to it, the first step is to find our target!

We know our target is in the range of 192.168.99.0/24 now using cidr notation with fping to find alive host fping -a -g 192.168.99.0/24 > scan.txt 2>/dev/null .

We know 192.168.99.70 is our tap0 IP assign to us by the VPN connection so the target is 192.168.99.50 now using nmap to scan our target.
Fingerprinting & Scanning
┌──(muzec㉿Muzec-Security)-[~/Desktop/Penetration]
└─$ nmap -sC -sV -oA nmap 192.168.99.50
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-28 11:54 WAT
Nmap scan report for 192.168.99.50
Host is up (0.58s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_clock-skew: mean: 6h29m53s, deviation: 4h57m01s, median: 2h59m51s
|_nbstat: NetBIOS name: ELS-WINXP, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:a5:b3:99 (VMware)
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: els-winxp
| NetBIOS computer name: ELS-WINXP\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-10-28T06:56:09-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 178.49 second
Closly looking at our nmap result we can know we are dealing with a windows operating system.
Installing Nessus

Downloaded but seems we need a activation.


Let Register for Nessus Essentials.

Done we can check our mail for the activation code but we are going to get to that part in a bit. now is time to install the nessus we downloaded.
dpkg -i Nessus-8.15.2-debian6_amd64.deb

Now let start nessus scanner.
/bin/systemctl start nessusd.service

Checking our mail for the activation code to activate our nessus.

User created now let wait the installing of the plugins and compiling take time.

In a bit.

Done now let set up a new policies for windows.

Smooth seems we have some really cool Vulnerabilities scanners.

But let click on advanced scan.

Now let click on DISCOVERY > PORT SCANNING .

Now let tick TCP .

Now let save it.

Now back to My scan and click on New Scan.

Click on User Defined.

Now let click on our new policies we created.

Add target and click on save.

Now let click on the icon to launch.

Completed now let check the result.

Now let export our report to see what we found export report in html.

Some very interesting reports vulnerabilities to exploit.
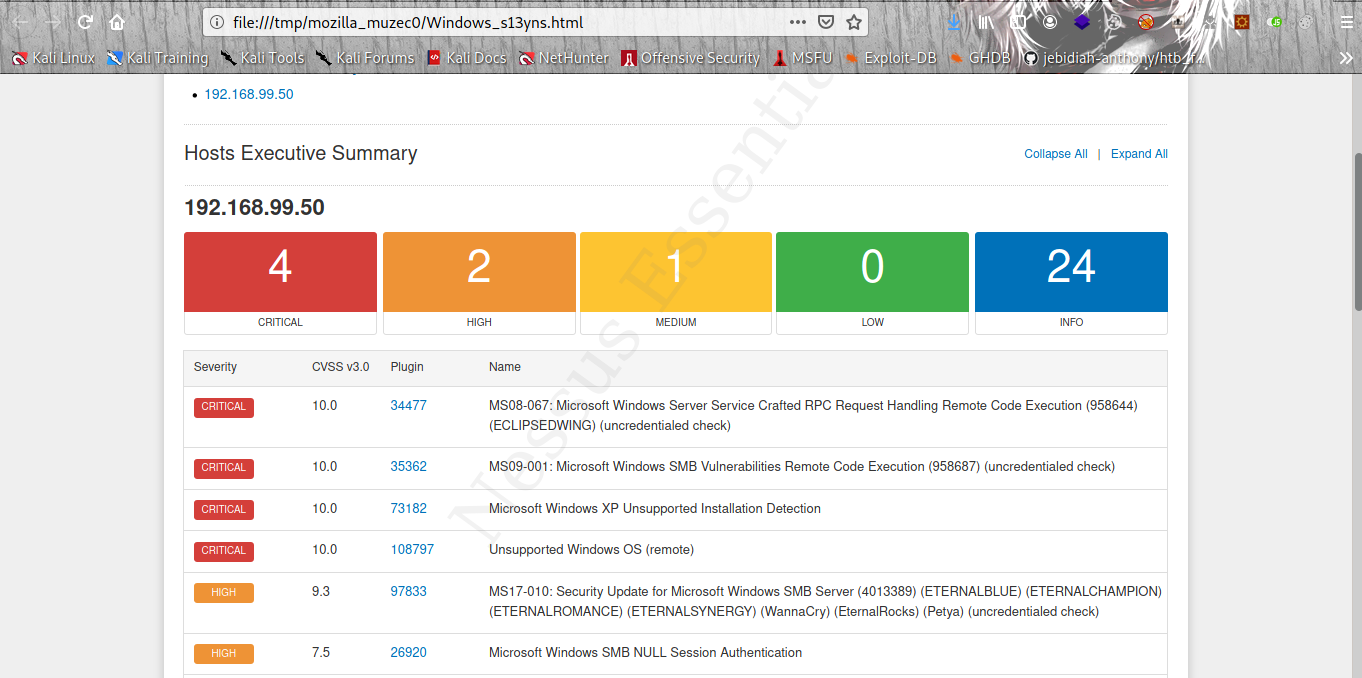
Vulnerabilities Exploitation With Metasploit
Let start with the first one:- MS08-067: Microsoft Windows Server Service Crafted RPC Request Handling Remote Code Execution (958644) (ECLIPSEDWING) (uncredentialed check)
Starting Msfconsole now let search the exploit.

Now let use the exploit.
use exploit/windows/smb/ms08_067_netapi
Setting up rhost and lhost rhost which is the target IP and lhost our listen address.

Now let exploit.

Boom exploit completed.
Now for the second one:- MS09-001: Microsoft Windows SMB Vulnerabilities Remote Code Execution (958687) (uncredentialed check)

Exploit that crashes the system.

Boom overflowing till it crashes.
Now for the third one:- MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (ETERNALBLUE) (ETERNALCHAMPION) (ETERNALROMANCE) (ETERNALSYNERGY) (WannaCry) (EternalRocks) (Petya) (uncredentialed check)

Setting it up before exploiting.

Now let exploit it.

Hmm interesting it vulnerable but the metasploit module is for x64 bit targets only you can use a quick python script to exploit it if you want to try it i think that from now see you next in the blackbox penetration testing series.
Hope you learn one or two from my article peace out guys.
Greeting From Muzec