Nmap Scanning………
Nmap -sC -sV -p- -oA nmap <Target-IP>
# Nmap 7.91 scan initiated Mon Oct 4 07:08:39 2021 as: nmap -sC -sV -p- -oA nmap 172.16.109.139
Nmap scan report for 172.16.109.139
Host is up (0.00021s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 94:fb:c0:76:f2:b3:ff:4a:ed:61:6a:ae:a1:ca:86:c1 (RSA)
| 256 d0:29:99:fd:69:68:21:e3:b4:a6:48:e4:4e:a1:7e:f4 (ECDSA)
|_ 256 2a:1b:1f:3d:ab:0a:00:5b:43:75:89:67:8a:98:21:df (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Did not follow redirect to http://may.hmv
10000/tcp open http MiniServ 1.979 (Webmin httpd)
|_http-title: 200 — Document follows
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Oct 4 07:09:18 2021 -- 1 IP address (1 host up) scanned in 39.71 seconds
We are having 3 open ports which seems interesting 22,80 and 10000 let start our enumeration on port 80 which is the HTTP.

Checking the page source we have nothing let hit some directory brute forcing.

Nothing also let brute force for sub-domain.

Adding to /etc/hosts file.

A login page seems interesting i try some sql injection no luck but seems we have some valid users i guess.
admin
marie
alice
Let try brute forcing the login page with burp suite with the valid users intercept request and send to intruder.

Payload Positions and attack type already selected prove of screenshot below:/

Payload tab:/

I decided to split my rockyou.txt password wordlist to make it easy.
head -n 50000 file.lst > rockyou50.txt
or
split -l 50000 file.lst rockyou50.txt

Passwordlist loaded now let hit on attack.

Boom we have credentials for marie let log in.

But man seems like a dead i check the source found nothing now time to check ssh.may.hmv .

A login page also trying the marie credentials but got no luck but something seems strange with the portal cookie when not give it a try on the ssh web page also.

Edit with cookie editor and we have our private key time to use SSH now.

We have user.txt time to get root.

We have write permission on the conf file now let try to abuse it to get root shell.
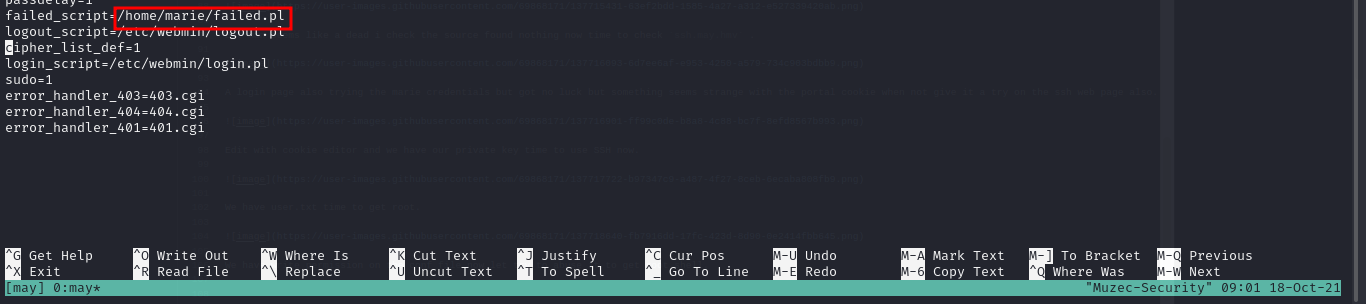
Generating Perl payload with msfvenom .

Transfer to the target.

Our listener is ready also now let access the webmin.

Putting a wrong credentials will give us a root shell.

Back to our listener.

We are root and done.
Greeting From Muzec