Enumeration With Nmap
We always start with an nmap scan…..
Nmap -sC -sV -oA nmap <Target-IP>
# Nmap 7.91 scan initiated Wed Oct 6 16:11:16 2021 as: nmap -sC -sV -p- -oA nmap 172.16.139.242
Nmap scan report for 172.16.139.242
Host is up (0.0024s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 fe:cd:90:19:74:91:ae:f5:64:a8:a5:e8:6f:6e:ef:7e (RSA)
| 256 81:32:93:bd:ed:9b:e7:98:af:25:06:79:5f:de:91:5d (ECDSA)
|_ 256 dd:72:74:5d:4d:2d:a3:62:3e:81:af:09:51:e0:14:4a (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Pwned....!!
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 6 16:11:27 2021 -- 1 IP address (1 host up) scanned in 11.28 seconds
We have three open ports and seems we don’t have access to the ftp server let give it a try.

But seems we have no access to FTP server now let check HTTP.
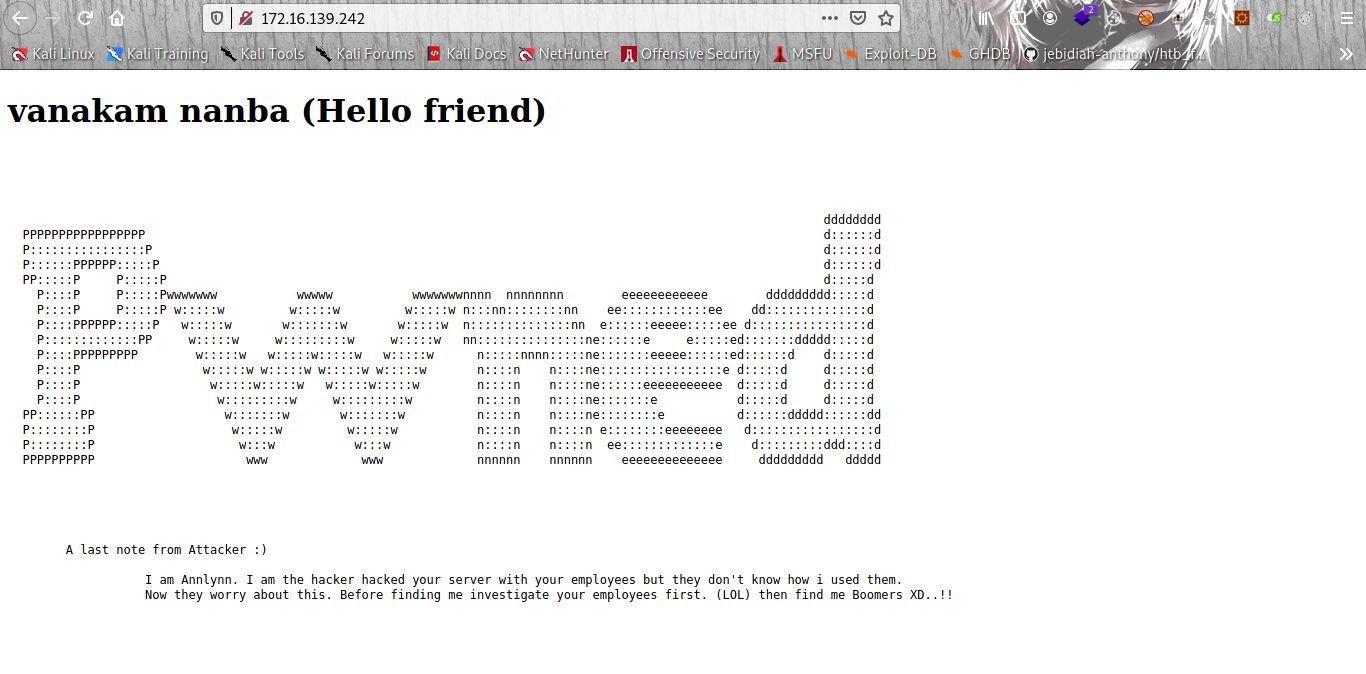
let check the page source.

But it not that helpful let burst some directories.

Checking robots.txt .

But it lead to a rabbit hole let use medium list to burst directories.

So let try accessing it man.

Cool a secret.dic file hehehehehehehe.

Let use the secret.dic to burst directories again.

Smooth let hit it.

Checking page source.

Boom we found credentials for FTP server smooth.

SSH private key and a note let get it to our machine.

Username for SSH let hit it.

We are in let get root.
Privilege Escalation

Ruuning sudo on the messenger.sh with user selena.

Spawn a tty shell and we are good.

Interesting we can see docker on the same group with selena let exploit it to gain root shell.
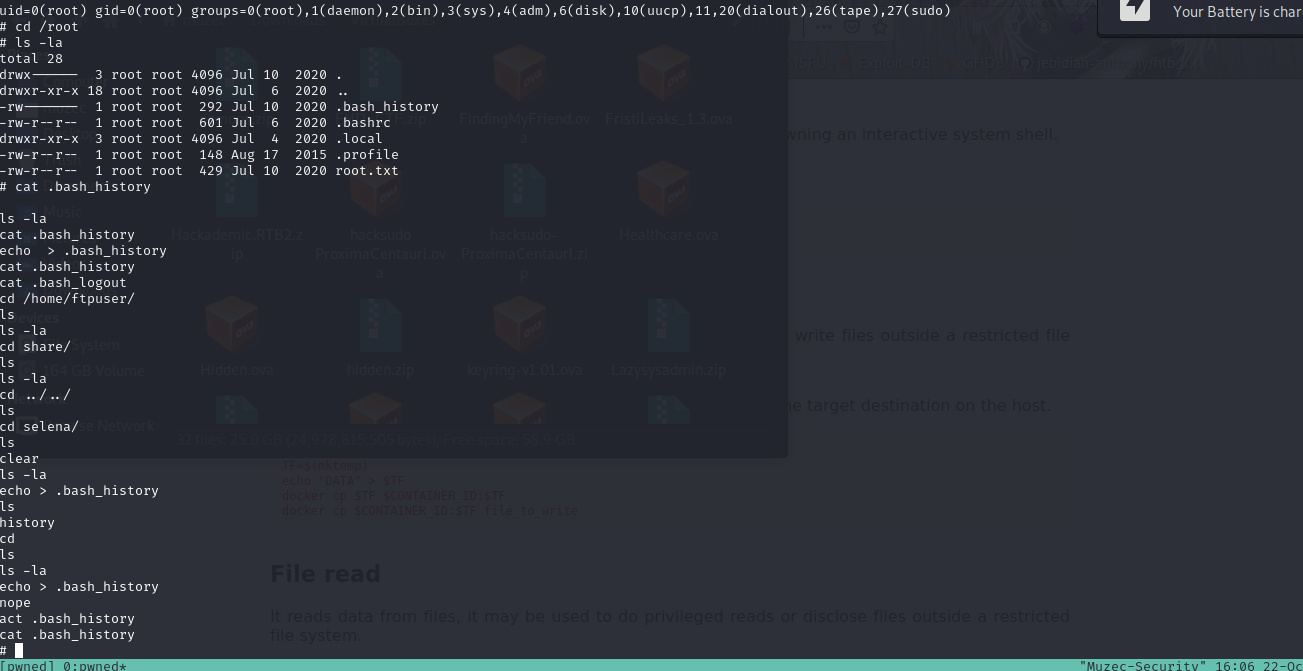
We are root and done.
Greeting From Muzec